Service Tokens
Provide restricted secrets access to applications in live environments.
A Doppler Service Token provides read-only secrets access to a specific config within a project.
It adheres to the principle of least privilege by ensuring an application only has access to a single config within a project for use in live environments.
Don't use a CLI or Personal Token in live environments as it provides write access with the same permissions as the account it was created by.
Requirements
- Doppler CLI
- Access to the config for a project you wish to provide access to
Creating Service Tokens
Dashboard
To generate a Service Token using the dashboard
- Go to the Project and select a Config
- Click the Access tab.
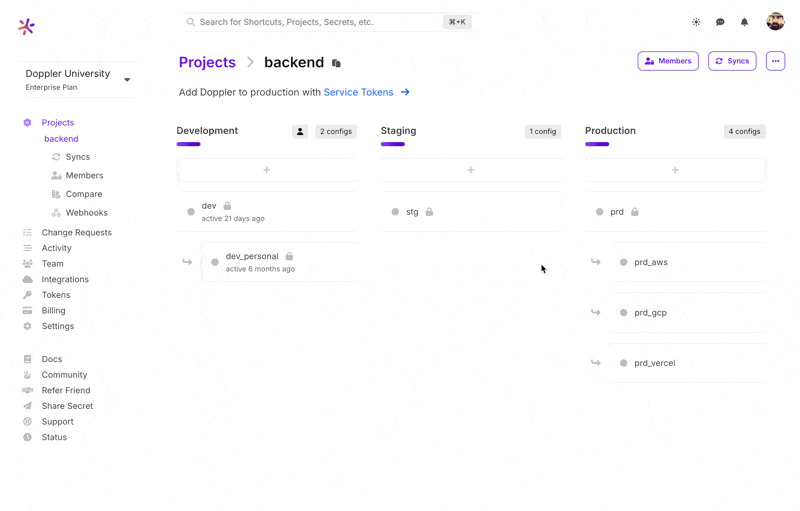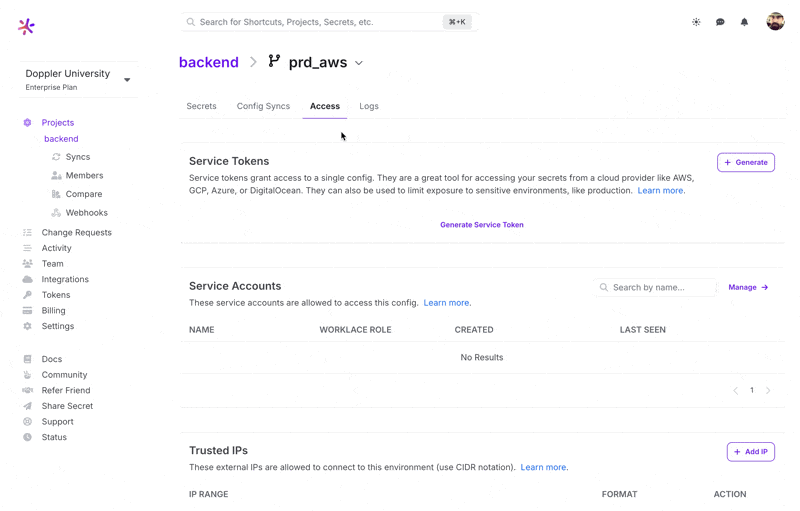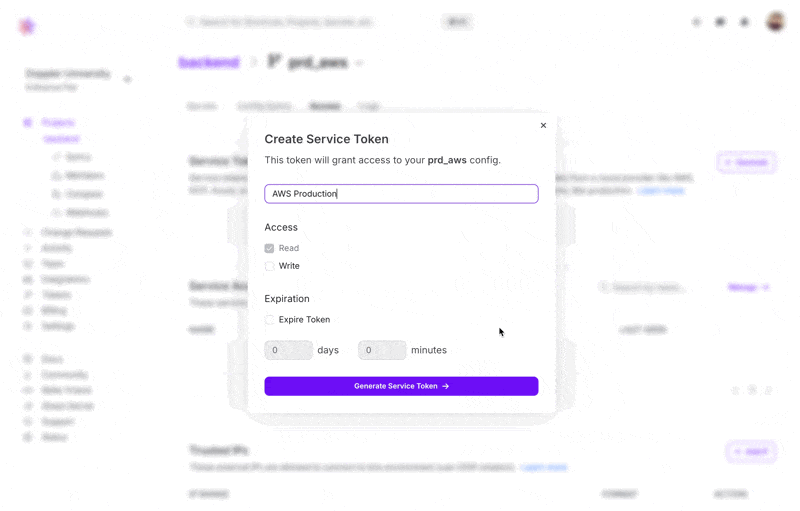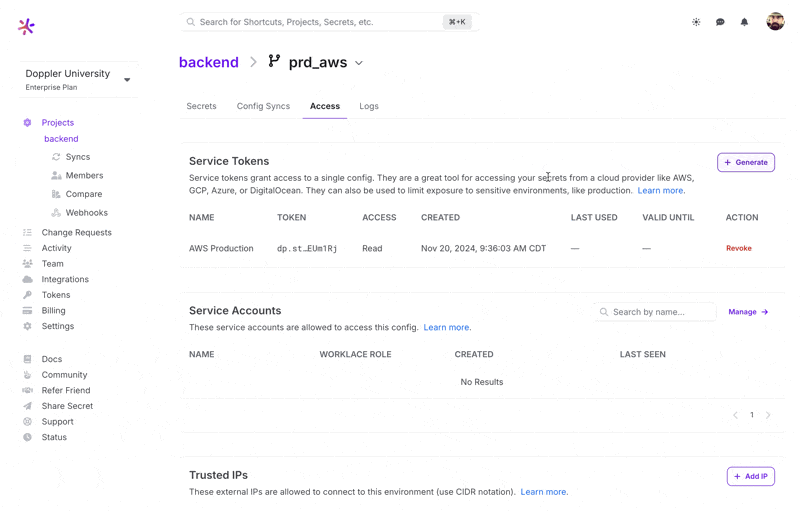
- Click on Generate.
- Provide a name for the token and optionally provide the token with write access or assign an expiration.
- Click on Generate Service Token
- Copy the Service Token as it is only shown once.
CLI
You can also generate a Service Token using the Doppler CLI:
# Select the project and config
doppler setup
# Create the Service Token
doppler configs tokens create token-name --plainYou can also create the Service Token in a single command by providing the project and config as arguments:
doppler configs tokens create --project your-project --config your-config token-name --plainUsing Service Tokens with the CLI
There are three ways to configure the Doppler CLI to use the Service Token.
Option 1: Persisted Service Token
This is the best option for Virtual Machines as it restricts which directory secrets can be fetched from and no additional configuration is required once registered (e.g. will persist across machine restarts).
# Prevent configure command being leaked in bash history
export HISTIGNORE='doppler*'
# Scope to location of application directory
echo 'dp.st.prd.xxxx' | doppler configure set token --scope /usr/src/app
# Supply secrets to your application
cd /usr/src/app
doppler run -- your-command-hereIf refreshing the Service Token, the doppler configure set token will need to be run again with the new Service Token value.
Option 2: The DOPPLER_TOKEN environment variable
DOPPLER_TOKEN environment variableThis method best suits environments where a Doppler integration sync isn't possible (e.g Render) or when secrets access to multiple configs are required (e.g. CircleCI jobs for staging and production).
The other common use case is when running your application via the shell or shell script:
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='export DOPPLER_TOKEN*'
export DOPPLER_TOKEN='dp.st.prd.xxxx'
doppler run -- your-command-hereWith Docker:
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='docker*'
docker container run -e DOPPLER_TOKEN='dp.st.prd.xxxx' your-app# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='export DOPPLER_TOKEN*'
export DOPPLER_TOKEN='dp.st.prd.xxxx'
docker-compose upOr Kubernetes:
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='kubectl create secret*'
# Create Kubernetes secret containing the Service Token
kubectl create secret generic doppler-token --from-literal=DOPPLER_TOKEN="dp.st.prd.xxxx"Inject SERVICE_TOKEN into your Kubernetes deployment:
apiVersion: apps/v1
kind: Deployment
...
spec:
containers:
- name: your-app
envFrom:
- secretRef:
name: doppler-tokenOption 3: The --token argument
--token argumentIt's also possible to use the --token option for doppler run:
# Prevent command with Service Token being recorded in bash history
export HISTIGNORE='doppler run*'
doppler run --token='dp.st.prd.xxxx' -- your-command-hereEphemeral Service Tokens
An ephemeral Service Token can be created by setting an expiration time. Once the duration is reached, the token is automatically deleted.
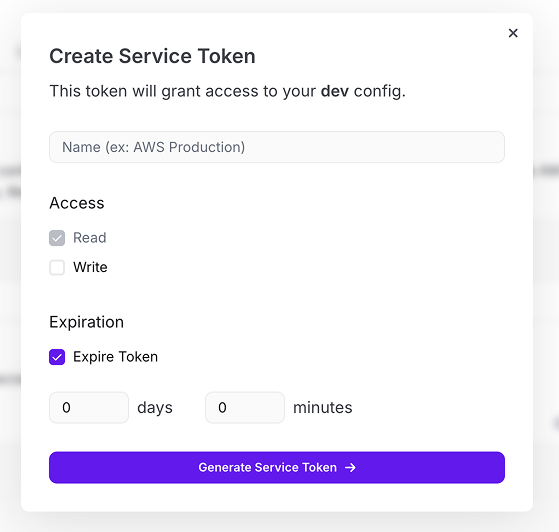
You can also create an ephemeral Service Token via the CLI using the --max-age option:
export DOPPLER_TOKEN=$(doppler configs tokens create ephemeral-token --max-age 1m --plain)Here's an example of using an ephemeral Service Token to provide temporary secrets access to a Docker container.
Revoking Service Tokens
Revoking a Service Token is non-reversible and immediately prevents secrets access.
Dashboard
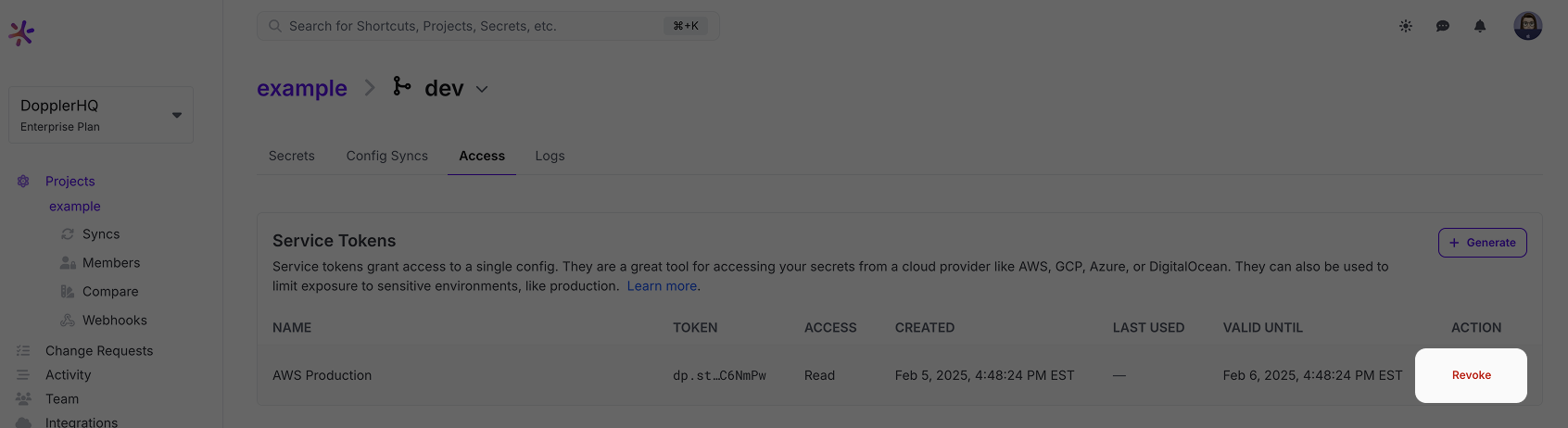
Revoking a Service Token from the Dashboard is performed from the Access tab for the Config by clicking Revoke.
CLI
Revoking a Service Token from the CLI can be done by executing the following command:
doppler configs tokens revoke -p PROJECT -c CONFIG dp.st.dev.fHhinxK...
Revoking a token and the secrets fallback fileIf a token is revoked, this will prevent access to the latest version of the secrets, but the CLI will continue to provide the last accessed version of the secrets (if it has previously been able to access the secrets) due to the encrypted fallback file being stored on disk.
Updated 9 months ago
