Trusted IPs
Trusted IPs require an upgraded subscriptionTrusted IPs are available with our Team and Enterprise plans. View our plans or book a demo for more details.
Only workplace Admins can manage Trusted IPs. Each config can define a set of trusted IP ranges, with each range represented in CIDR block notation (for example, 183.27.224.0/24). Only client requests originating from within a trusted IP range will allow access to the config. Use trusted IP ranges to restrict traffic to configs that come from your corporate networks or a CDN service that proxies traffic.
When a new config is created, it is configured with a default trusted IP range of 0.0.0.0/0 which will admit traffic from the public internet.
Trusted IP ranges only restrict access to API endpoints that interface with the given config. They do not control which source IP ranges can login to the Dashboard.
Let's now configure a trusted IP to only allow access from a corporate IP address range.
Remove Global Whitelist
To create a Trusted IP, go to a project and then select a config. From there, select the Access tab.
First, prevent global access by clicking the Remove button on the 0.0.0.0/0 row.
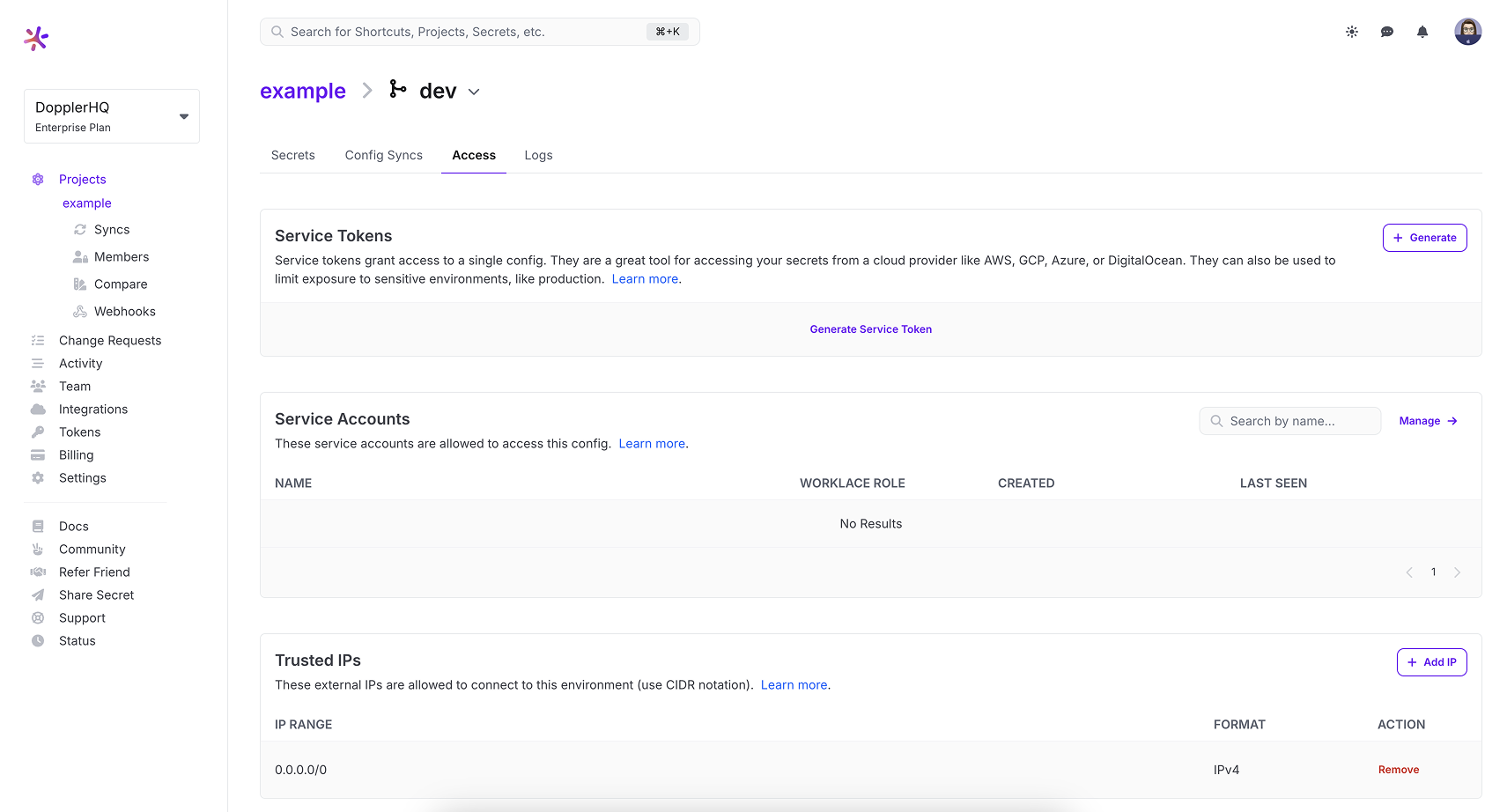
This will open up a confirmation modal. To confirm, click the Remove button.
Add Trusted IPs
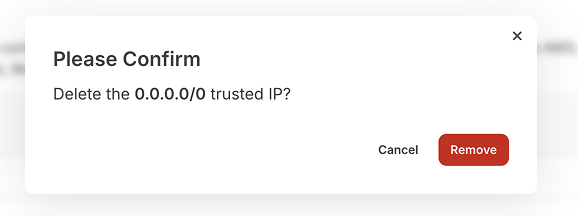
Now that the global IP range has been removed, you should not see any trusted IPs in the list. This will disallow all connections.
Let's add your corporate network's IP ranges one at a time. To add a Trusted IP, click the Add Trusted IP button. This will open a dialog.
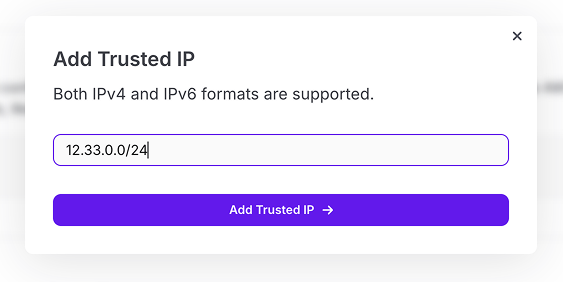
Once you have added the IP range and clicked the submit button you should see the IP range in your list.
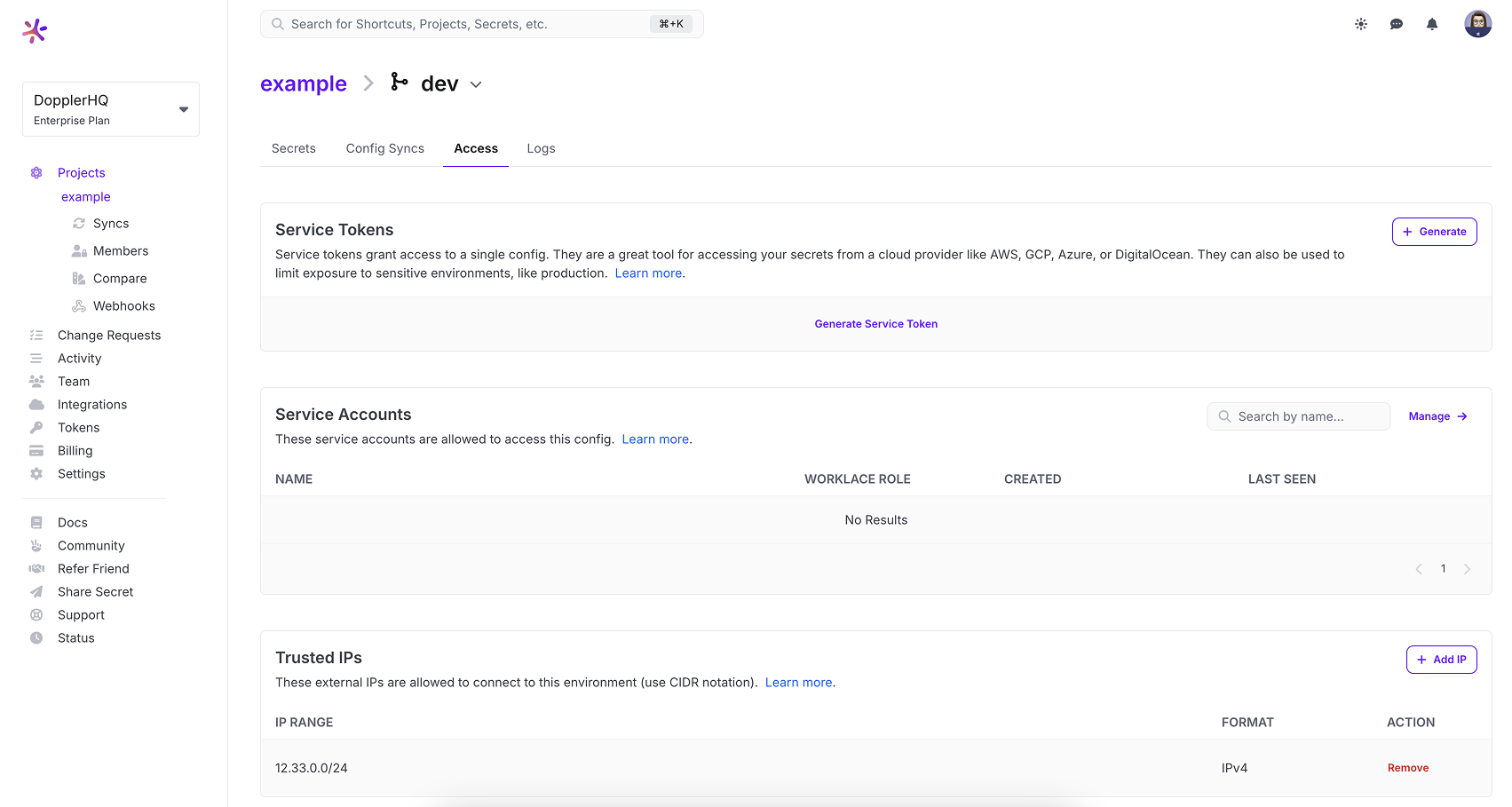
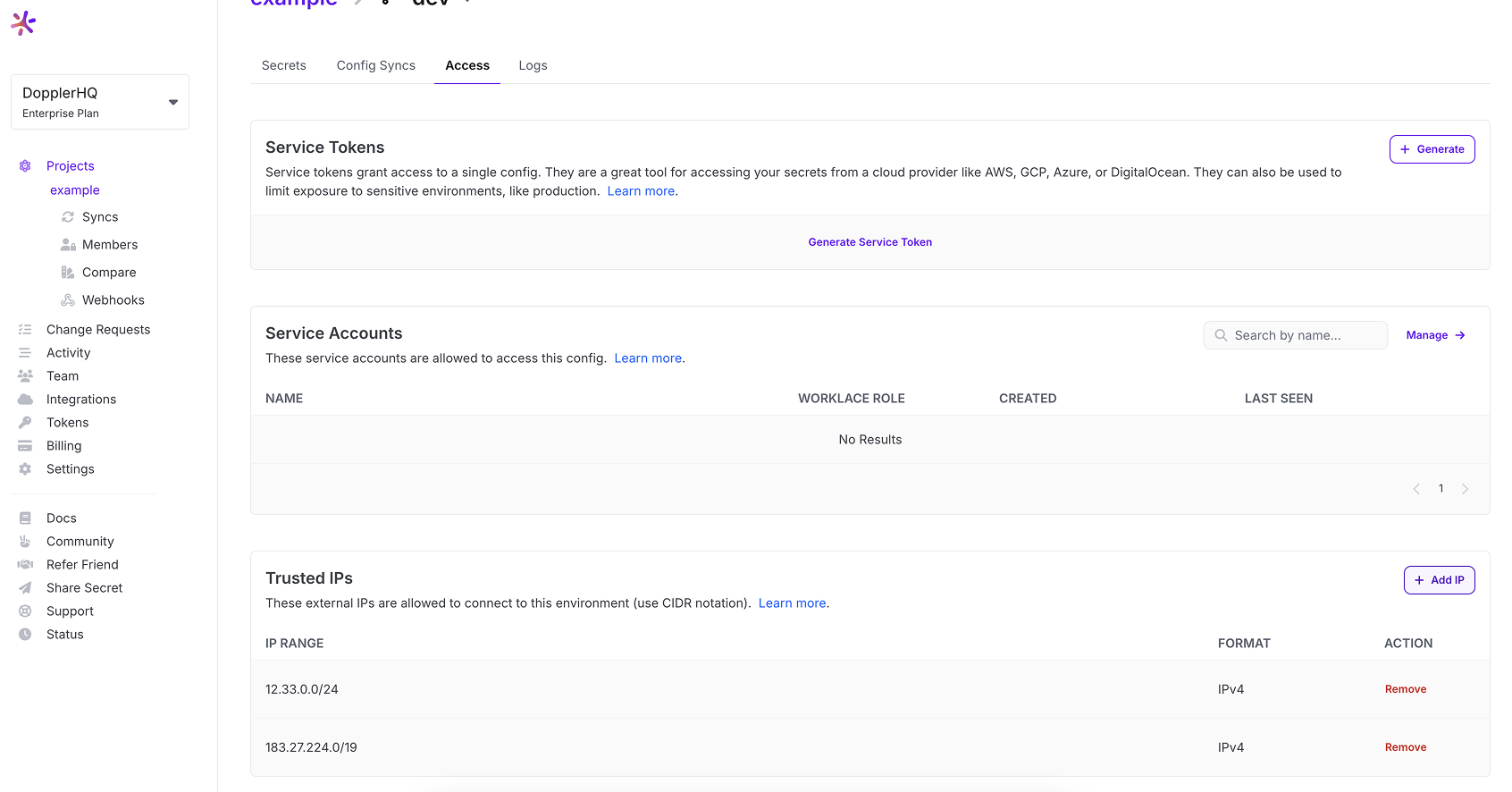
This can be repeated should you need to define multiple IP address ranges.
Updated 5 months ago
