Multi-Factor Authentication (MFA)
Learn how to enable MFA on your Doppler account.
Given the prevalence of weak and reused passwords on the internet, multi-factor authentication is an essential step for securing your online accounts. By default, Doppler enforces email-based MFA, requiring you to enter a code emailed to you. This ensures that the person signing in has access to the email address associated with the Doppler account. Doppler supports other popular forms of MFA, including OTP and security keys (e.g., Yubikeys).
If the Multi-Factor Authentication section of your Account Settings isn't showing up, it's because you've logged in via a form of SSO (e.g., Google Auth, GitHub Auth, SAML SSO, etc.). Doppler's MFA features are disabled in those scenarios because the identity providers being used have their own MFA protections, making additional protections on Doppler's end redundant. In these situations, make sure you have MFA enabled with the SSO provider you're using!
Email-based MFA
Every Doppler account has email-based MFA enabled by default. This means that when you login, a verification email is sent to the account's address with a code that must be entered before you can access your account.
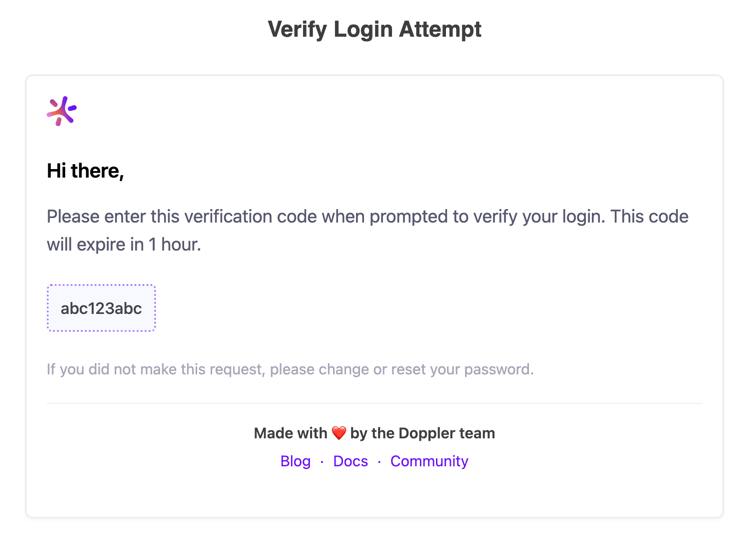
If you'd rather use another MFA method, you can enable one of the other options mentioned below and you'll be prompted for those rather than being sent verification emails!
One-Time Password (OTP)
One of the most popular forms of MFA is using One-Time Passwords (OTP) via an authenticator application such as 1Password or Google Authenticator. You can configure your account to use this by accessing your account settings by choosing the Account option from the Avatar menu in the top right corner of the dashboard. From there, scroll down to the Multi-Factor Authentication section and click the Configure link next to One-Time Password.
This will walk you through a typical MFA OTP setup process that allows you to add it to your authenticator application of choice. After enabling OTP, you'll be prompted to generate Recovery Codes. Be sure to generate these and store them somewhere secure (e.g., the notes field in the 1Password entry for your Doppler account). In the event you lose access to the device you're using as your authenticator, you'll be able to use these Recovery Codes to gain access to your account and disable OTP, so you can set it up on a new device!
Make sure you generate Recovery Codes and store them in a safe place so you can gain access to your account in the event you lose access to your authenticator! We're unable to perform MFA resets on accounts, so this is especially important!
Security Keys
If you prefer to have a physical secondary authentication form, then a security key (e.g., Yubikey, Touch ID, Face ID) is the way to go! You can configure your account to use this by accessing your account settings by choosing the Account option from the Avatar menu in the top right corner of the dashboard. From there, scroll down to the Multi-Factor Authentication section and click the Configure link next to Security Keys.
This will walk you through the process of registering the security key with your account. Once configured, you'll be prompted for your security key when authenticating with Doppler.
We recommend that you setup at least two security keys so that you have a backup in the event that you lose one of your keys.
MFA Recovery
Doppler is unable to reset MFA on your account but there are a few mechanisms you can use to recover your account if your MFA device is lost or damaged:
- If you have OTP MFA configured, you can use a recovery code to sign in
- If you are signed into the Doppler CLI, you can generate a one-time-use recovery code with
doppler mfa recovery
If possible, always setup several MFA methods. If you lose access to all of your MFA methods, you will be unable to recover your account and will have to create a new account with a different email address.
Updated 4 months ago
