GCP Cloud Build
This guide will show you how to use the Doppler CLI to supply secrets as environment variables for GCP Cloud Build.
Prerequisites
- You have an existing GCP project and are familiar with Cloud Build and IAM permissions
- You have enabled the Secret Manager API for your GCP project
- Experience in using GCP Secret Manager is advantageous but not required
Doppler Service Token Storage
To supply secrets in Cloud Build, the Doppler CLI requires a Service Token and there are two methods for storing this token in GCP:
We recommend using Secret Manager for encrypted storage and the ability to use IAM roles to restrict secret access to the Cloud Build service account and authorized users.
In contrast to Secret Manager, Trigger Substitution Variables are visible and editable by anyone that has access to Cloud Build triggers.
GCP Secret Manager
Using GCP Secret Manager to provide secrets for Cloud Build is the most secure storage and access mechanism for the Doppler Service Token.
Create a Service Token to provide read-only access to a specific config, then copy the Service Token value.
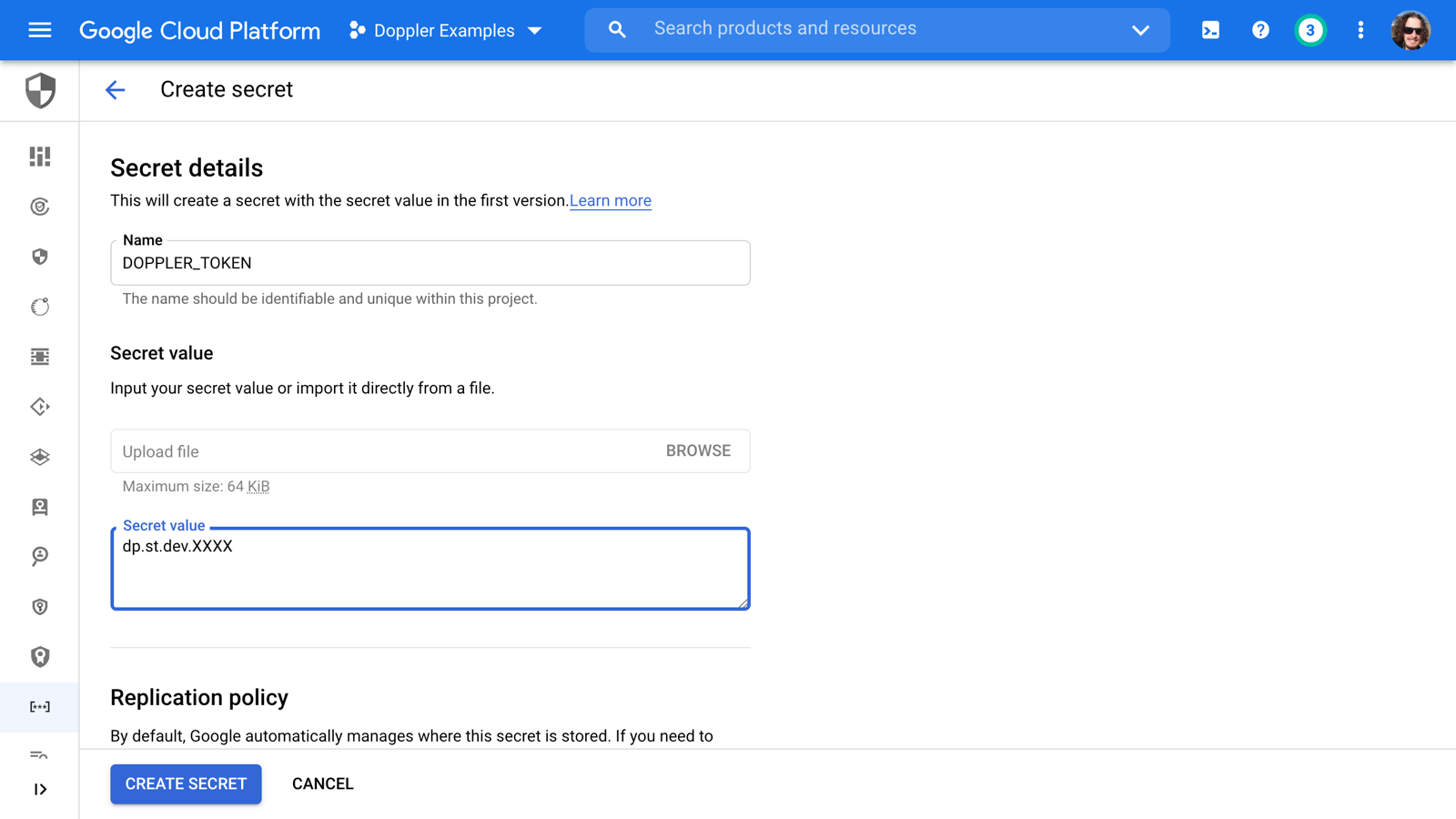
Go to the Secret Manager console, then create a new secret in GCP Secret Manager named DOPPLER_TOKEN containing the service token value, then click the CREATE SECRET button.
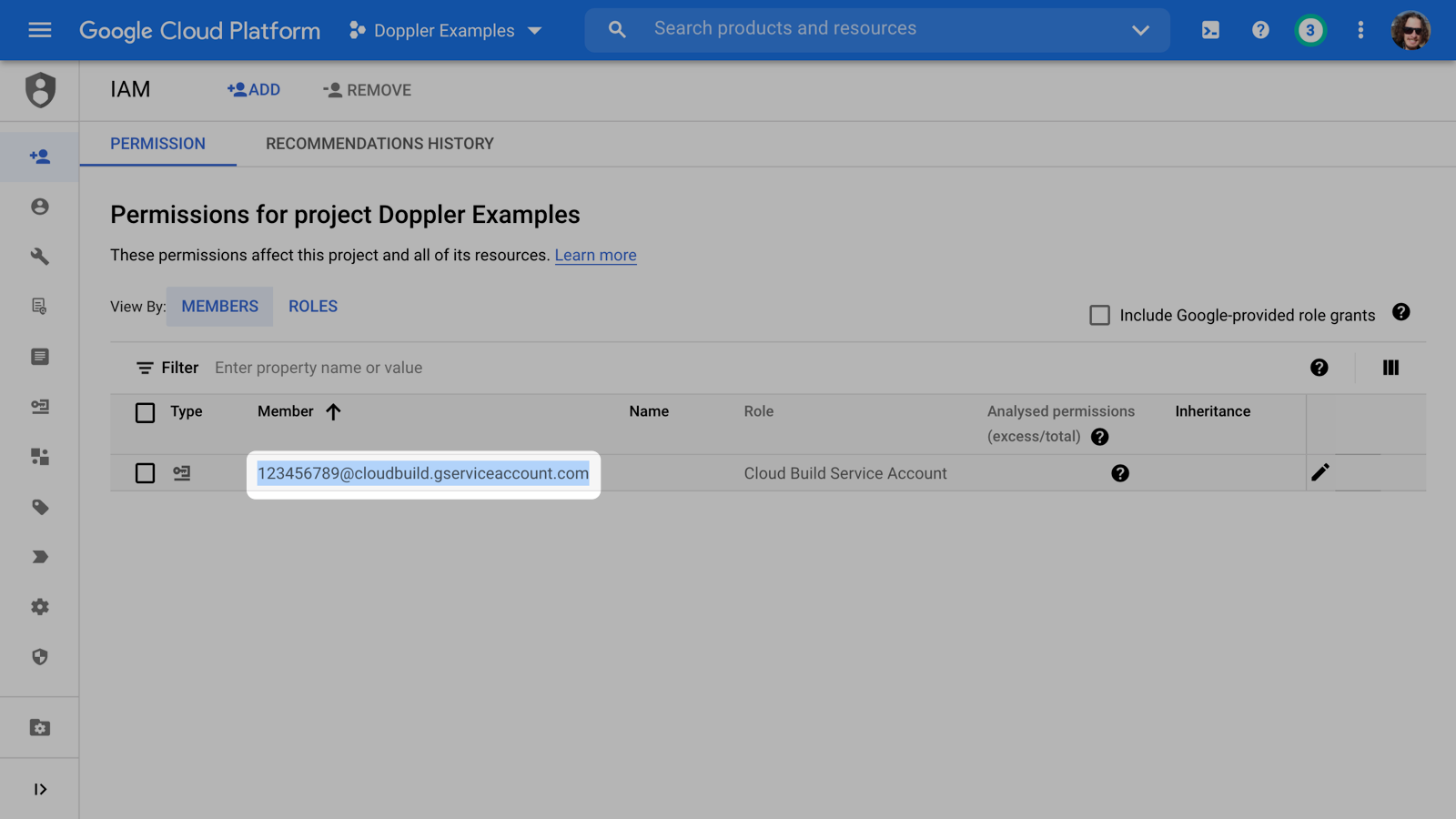
Now let's give the Cloud Build service account access to the DOPPLER_TOKEN secret and to do this, we need the email belonging to the Cloud Build Service Account (learn more in the Cloud Build access docs).
To find this, head to the IAM console and copy the email address belonging to the Cloud Build Service Account.
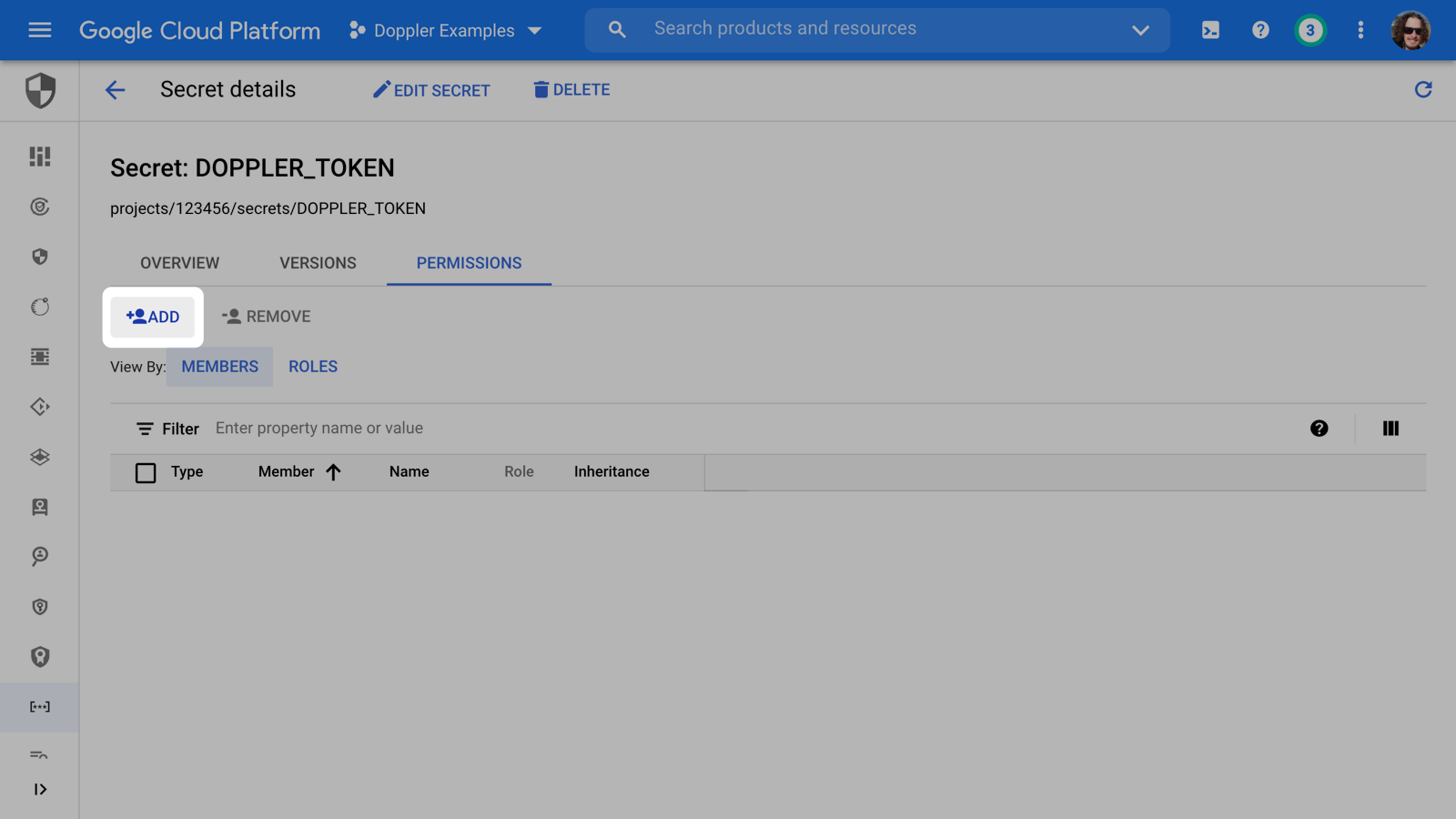
Next, head back to the Secret Manager console, click on the DOPPLER_TOKEN secret, and under the PERMISSIONS tab, click the ADD button.
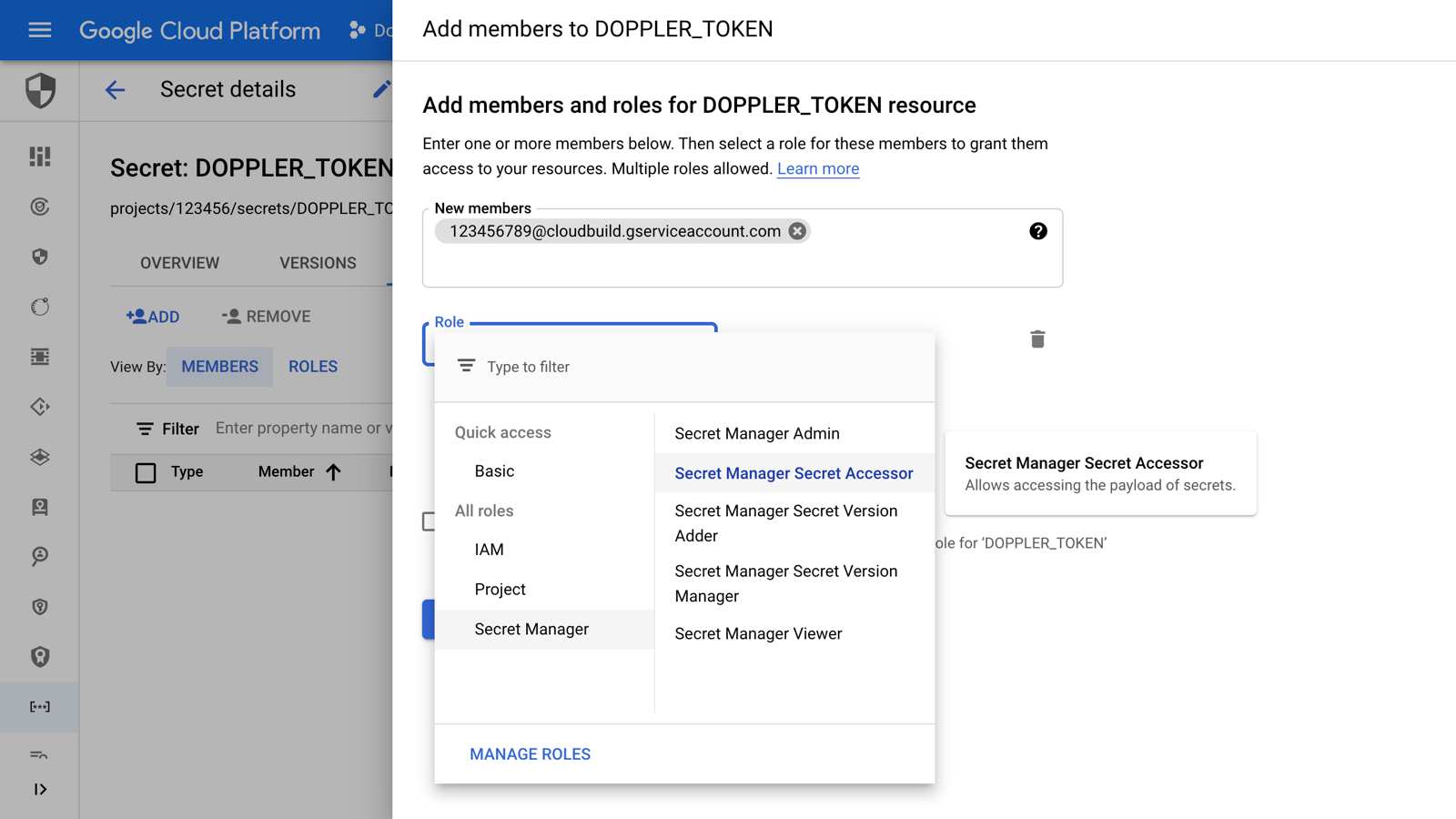
Paste in the Cloud Build Service Account email address, and select the Secret Manager Secret Accessor IAM role, then click the SAVE button.
Now that Cloud Build can access the DOPPLER_TOKEN secret, the next step is to create or modify your Cloud Build file to:
- Install the Doppler CLI
- Fetch the
DOPPLER_TOKENsecret using theavailableSecretsdefinition - Populate the
DOPPLER_TOKENenvironment variable using thesecretEnvfield - Use the Doppler CLI to supply secrets to your build scripts or commands
A complete example could look like the following:
steps:
- name: ubuntu
entrypoint: bash
args:
- -c
- apt-get update > /dev/null &&
apt-get install -y curl gnupg > /dev/null &&
(curl -Ls --tlsv1.2 --proto "=https" --retry 3 https://cli.doppler.com/install.sh || wget -t 3 -qO- https://cli.doppler.com/install.sh) | sh &&
doppler run -- ./your-build-script.sh;
secretEnv: ['DOPPLER_TOKEN']
availableSecrets:
secretManager:
- versionName: projects/your-project/secrets/DOPPLER_TOKEN/versions/latest
env: DOPPLER_TOKENTrigger Substitution Variable
User-defined Trigger Substitution Variables is the easiest method to set up but don't provide the same level of security compared with GCP Secret Manager.
To use this method, first create a Service Token to provide read-only access to a specific config, then copy the Service Token value.
Now either create or edit an existing Trigger and create a new Substitution variable named _DOPPLER_TOKEN containing the service token value, then click the SAVE button.
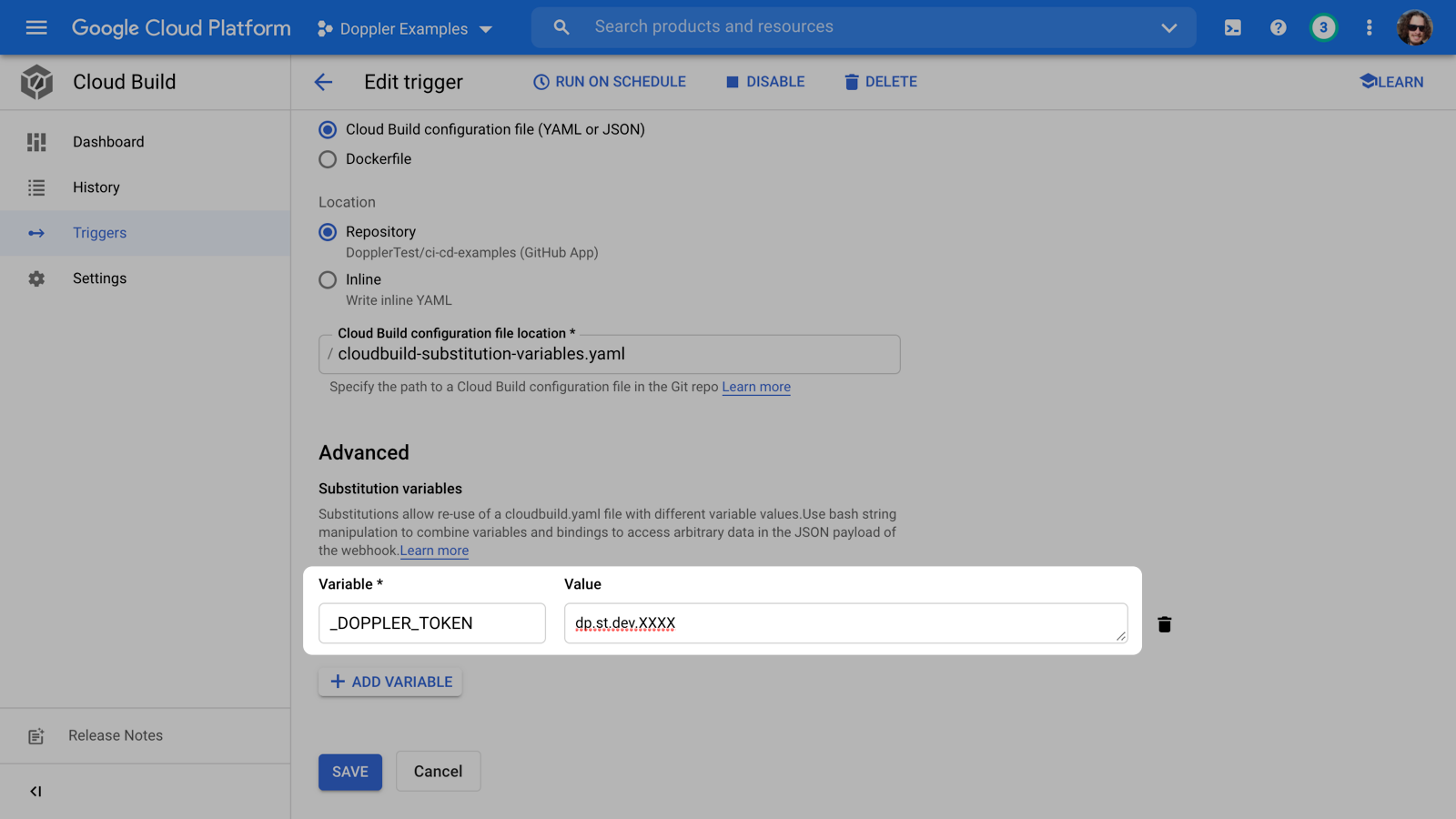
Then create or modify your Cloud Build file to:
- Install the Doppler CLI
- Set the value of the
DOPPLER_TOKENenvironment variable to the_DOPPLER_TOKENsubstitution variable - Use the Doppler CLI to supply secrets to your build scripts or commands.
A complete example could look like the following:
steps:
- name: ubuntu
entrypoint: bash
args:
- -c
- apt-get update > /dev/null &&
apt-get install -y curl gnupg > /dev/null &&
(curl -Ls --tlsv1.2 --proto "=https" --retry 3 https://cli.doppler.com/install.sh || wget -t 3 -qO- https://cli.doppler.com/install.sh) | sh &&
doppler run -- ./your-build-script.sh;
env:
- DOPPLER_TOKEN=$_DOPPLER_TOKEN
Amazing Work!Now you know how to use Doppler CLI to supply secrets as environment variables for GCP Cloud Build.
Updated 4 months ago
