GCP Service Account
Doppler supports rotating GCP Service Accounts keys. Rotating the underlying service account keys instead of the key object itself improves auditability and consistency within your infrastructure while maintaining a strong security posture.
Requirements
- Understand the Doppler rotation methodology
- GCP Account with the ability to create GCP Service Accounts
Overview
GCP Service Accounts are an account type that can be used programmatically for authentication. Specifically, Doppler supports rotating service accounts leveraging user-managed key pairs. GCP supports up to ten active key pairs for a service account, though Doppler requires that no more than eight key pairs exist to guarantee that Doppler can always generate new keys.
Two service accounts are involved in the rotation process - the service account whose keys are actually rotated and a service account for Doppler to utilize (impersonate) to perform the rotation. The service account Doppler uses for account impersonation can be utilized to rotate any number of service account keys.
Service Account Impersonation
To perform GCP Service Account key rotation, Doppler 'impersonates' a finely scoped service account that you create in your account. After impersonating the service account, the GCP APIs are used to perform key rotation.
When creating the impersonation service account, a custom, one-off slug is entered in the service account description. Doppler uses this as a second verification parameter in order to combat the confused deputy problem, as GCP does not have a native mechanism for this like AWS does.
Configuration
Enable the IAM API
- Enable the IAM API in your GCP project if it isn't already
Optional: Add Doppler's Google Workspace ID if Domain Restricted Sharing is enabled
If Domain Restricted Sharing is enabled on your GCP project or organization, you need to add Doppler's workspace ID to the allowed entries.
- Navigate to the domain restricted sharing policy within GCP Organization Policies
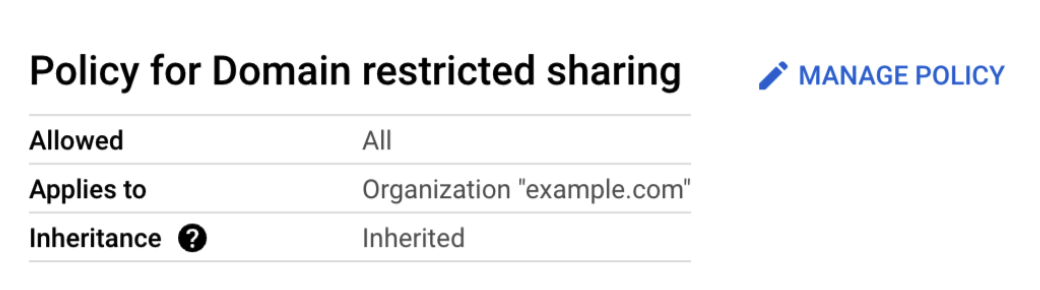
- Select Manage Policy
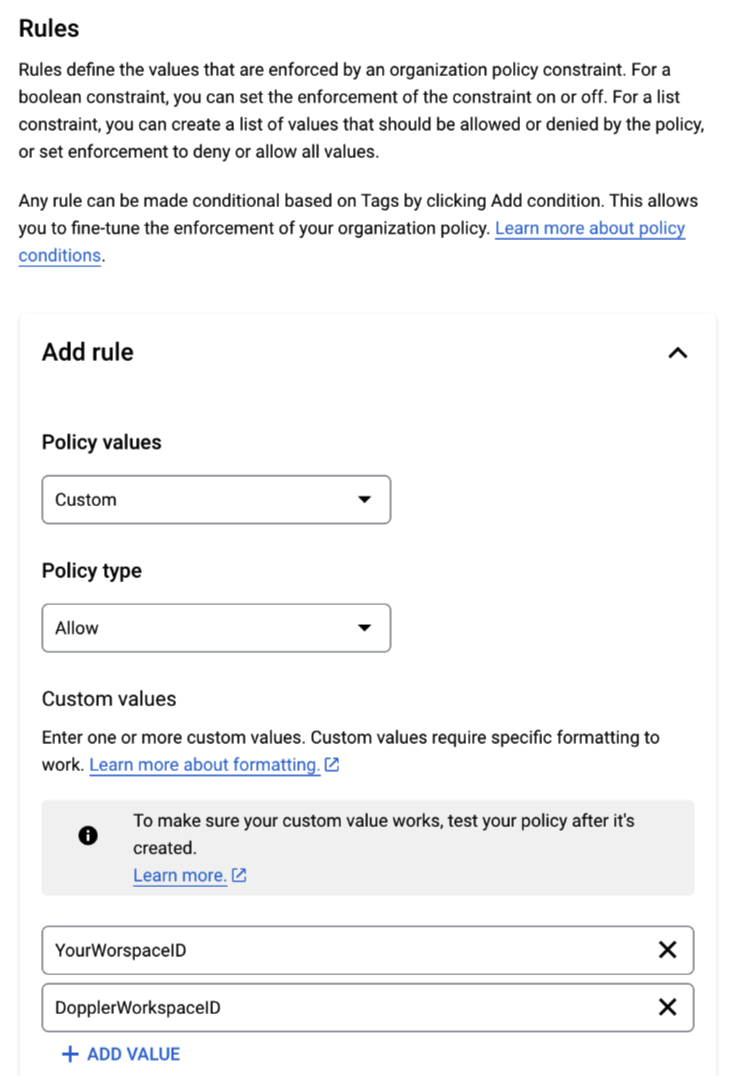
- Under Rules, add Doppler's workspace ID
C03c9go8jusing a Custom Allow rule. Save it.
Create the Service Account for Impersonation
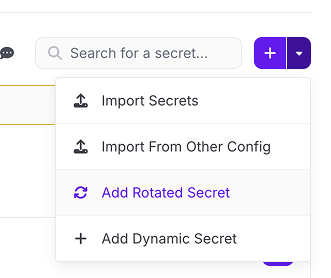
- Navigate to the Doppler config you would like to add a rotated secret to
- Click the dropdown next to Add Secret and select Add Rotated Secret
- Name your rotation integration
- Make note of the impersonation slug - you will use it below
- In a new browser tab, navigate to Service Accounts within the IAM & Admin
- Select Create Service Account
- Name your service account, with a good example being
DopplerImpersonationSA - In the description, enter the slug displayed in the rotated secret creation workflow above; it will be in the format of
doppler_impersonate:<slug> - Select Done
- From the Service Accounts table, select the service account you just created
- On the service account's Details tab, copy the service account's email address
- Go to the Permissions tab
- Select Grant Access
- Paste the service account email in the Principals input and hit tab. You will be granting the service account access to itself.
- Change the Role to
View Service Accounts - Select Save
- Select Grant Access again.
- Under Principals enter
[email protected]and assign it the rolesService Account Token CreatorandView Service Accounts - Select Save
- Enter the service account email in the Doppler UI and hit Next
Configure the Service Account to Rotate
- In GCP, If you do not already have a Service Account to rotate, create one and configure it accordingly
- Navigate to its details page and then its Permissions tab
- Select Grant Access and in the Principal input, enter the email for the impersonation service account created above
- Enter
Service Account Key Adminfor the role- Note: the impersonating service account - i.e. Doppler - will only be able to modify this specific service account's keys
- From the Details tab for the service account to be rotated, grab the service account email.
- In the Doppler UI, enter the service account email in the corresponding input
- Select the interval the key pairs should be rotated at. Hit Next to finish setup
Behind the scenes, Doppler created a new key pair for the service account and injected it into the Doppler config. The next key pair will be created at the interval defined during setup
Injected Values
After creating the GCP Service Account keys rotated secret, two individual secrets will be available in the config. Doppler ensures the active secret instance is returned when requested or synced. Each is prefixed with the name of your rotated secret.
- KEY_NAME - the ID of the GCP Service Account key pair
- KEY - the private key for the GCP Service account key pair
Updated 4 months ago
