Azure DevOps Pipelines
Learn how to easily manage environment variables for your Azure DevOps Pipelines.
This guide will show you how to use Doppler to provide secrets to pipelines in Azure DevOps.
Prerequisites
- You have created a project in Doppler
- You have an Azure Devops account
Azure DevOps Environment
Create a custom Azure DevOps environment so CI/CD secrets are maintained separately from application secrets.
Service Tokens
Create a Doppler Service Token for the Azure DevOps config and copy it to your clipboard.
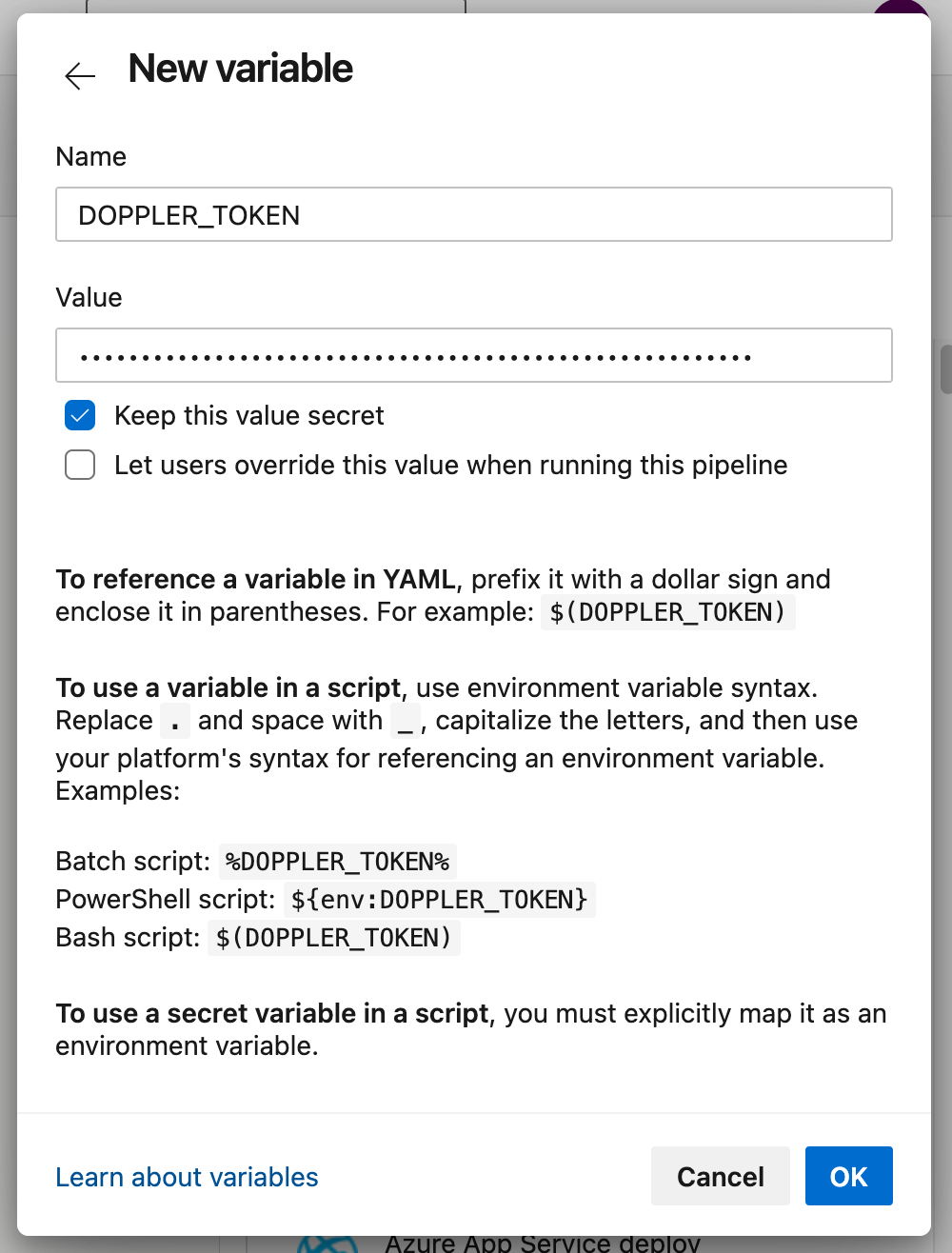
Then in Azure DevOps, go to your pipeline Variables > + (new variable) and add a new variable DOPPLER_TOKEN using the token content copied to the clipboard.
Check the Keep this value secret option, then click Ok to save the variable.
Your Azure DevOps pipeline will now be able to access all the secrets in that Doppler config on each job run.
Usage
Now, let's create a simple pipeline to show you how to use the Doppler CLI in your pipeline scripts.
First install the Doppler CLI, then inject secrets as environment variables into your build script or commands using the doppler run command.
trigger:
- main
pool:
vmImage: ubuntu-latest
steps:
- script: |
(curl -Ls --tlsv1.2 --proto "=https" --retry 3 https://cli.doppler.com/install.sh || wget -t 3 -qO- https://cli.doppler.com/install.sh) | sudo sh
displayName: Install Doppler CLI
- script: doppler run -- ./bin/build.sh # Replace with your build command or script
displayName: Build
env:
DOPPLER_TOKEN: $(DOPPLER_TOKEN)The
envfield is required for scripts using the Doppler CLI as secret variables must be explicitly mapped to environment variables.
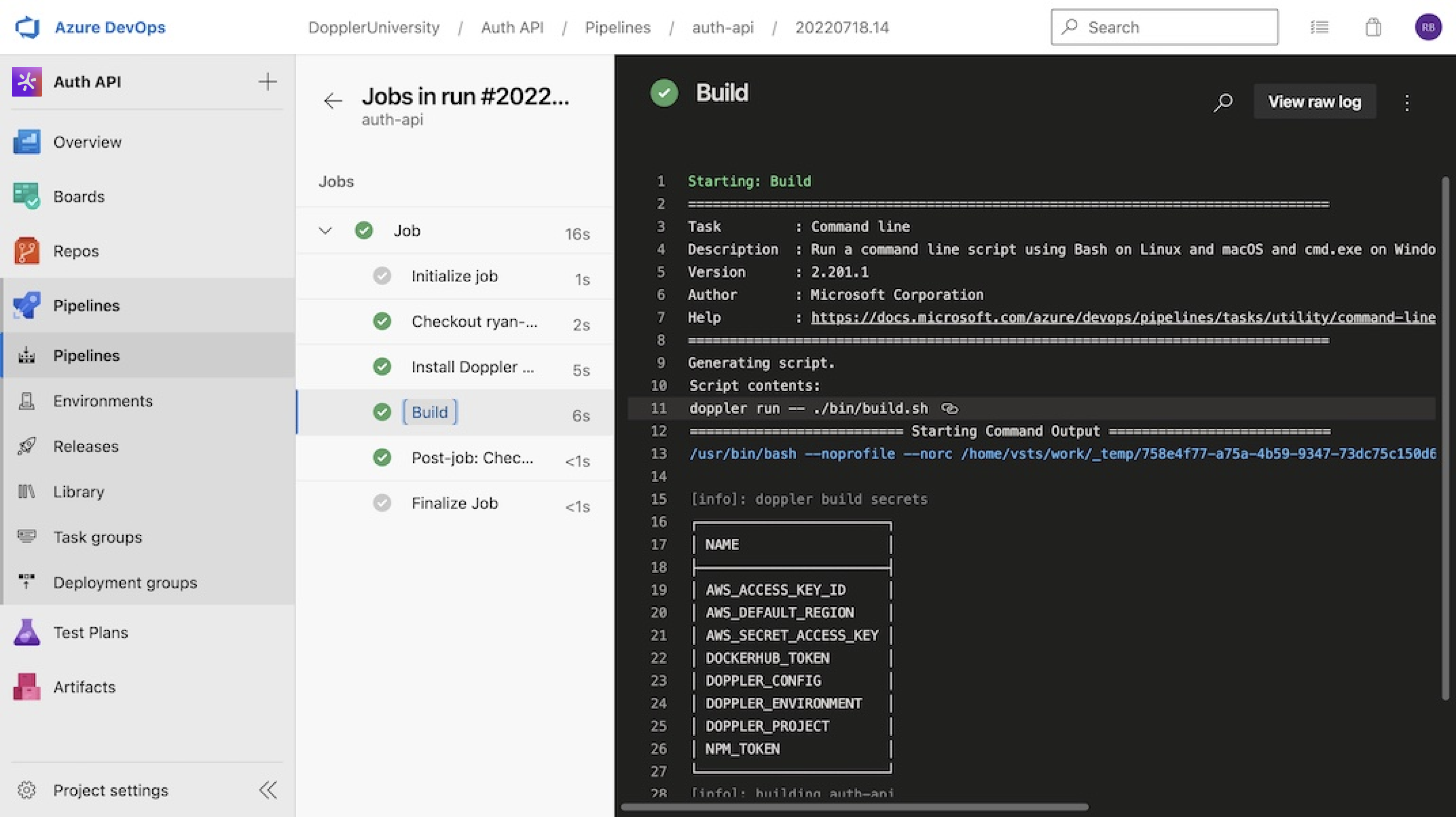
Save the pipeline and run it. The Azure DevOps pipeline job shows the successful installation of the CLI and fetching of a secret.
Amazing Work!Now you know how to configure Azure DevOps pipelines to fetch secrets from Doppler.
Updated 5 months ago
