External Secrets Operator
Kubernetes secrets sync automation using the External Secrets Operator Doppler provider.
If you're already using the External Secrets Operator in your Kubernetes cluster, then you can take advantage of our Doppler External Secrets provider.
If you're after an in-depth end-to-end user guide, check out our Kubernetes External Secrets blog post.
Authentication
Doppler Service Tokens are recommended as they restrict access to a single config.
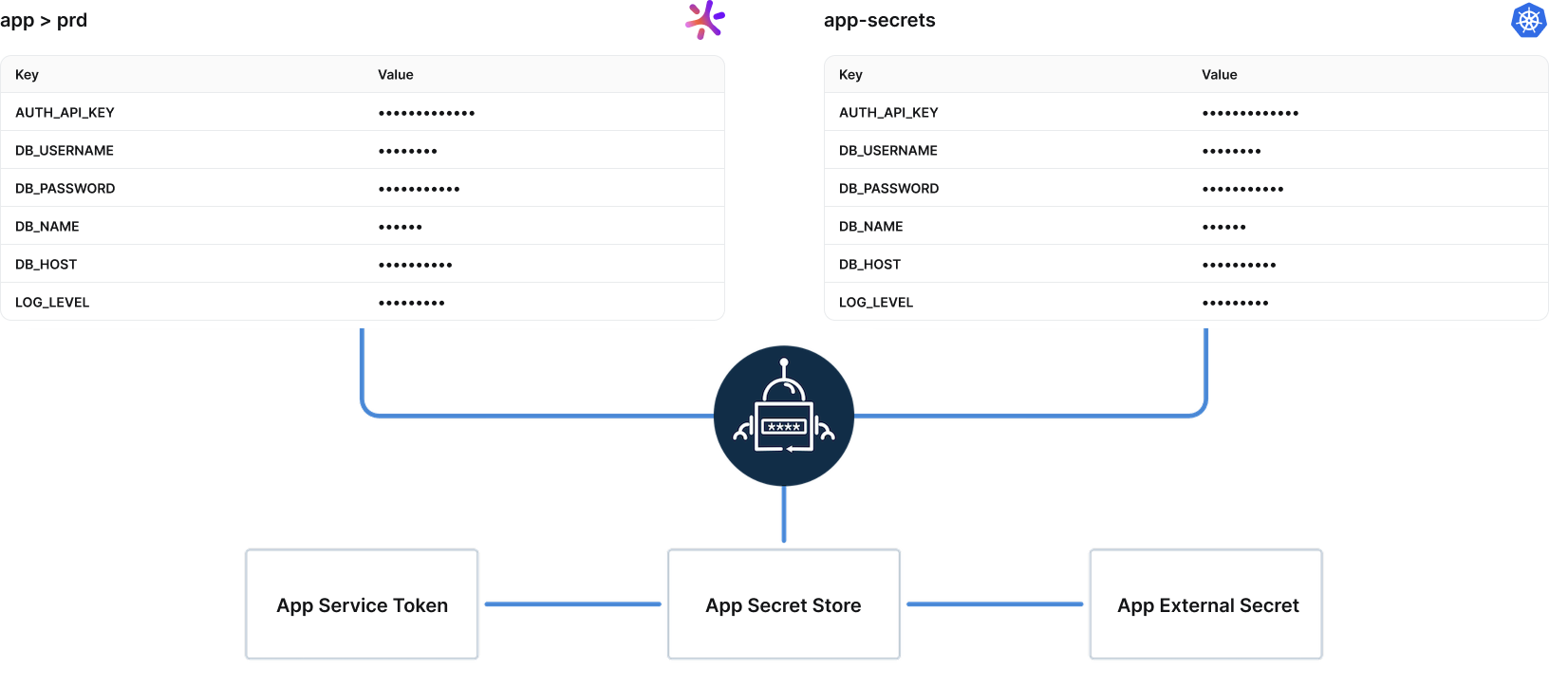
Doppler Service Account Tokens are also supported but require
projectandconfigto be set on theSecretStoreorClusterSecretStore. See the Service Account Token example below.
Create the Doppler Token secret by opening the Doppler dashboard and navigating to the desired Project and Config, then create a new Service Token from the Access tab:
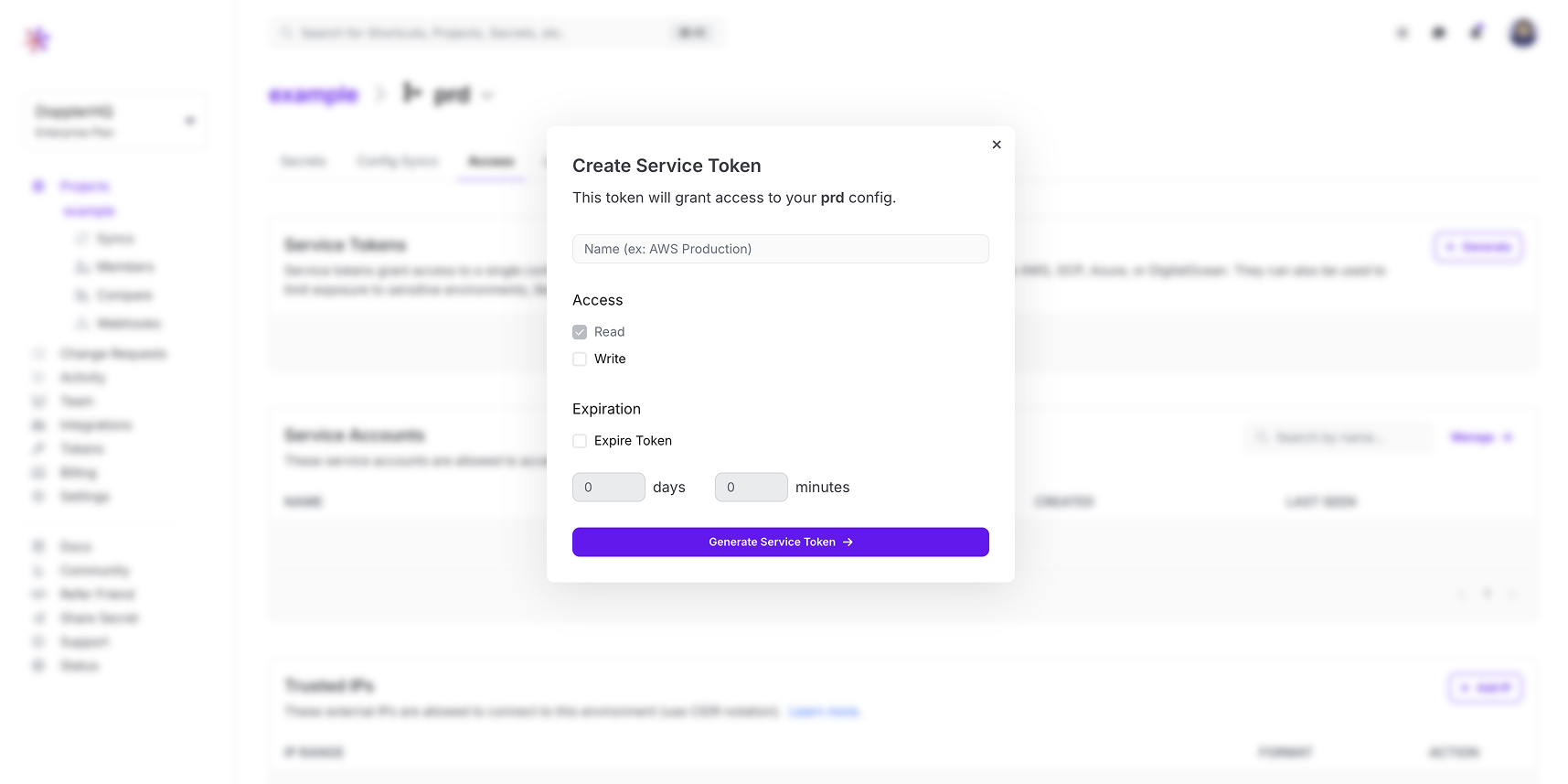
Create the Doppler Token Kubernetes secret with your Service Token value:
HISTIGNORE='*kubectl*' kubectl create secret generic \
doppler-token-auth-api \
--from-literal dopplerToken="dp.st.xxxx" \
-n external-secretsThen to create a generic SecretStore:
apiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: doppler-auth-api
spec:
provider:
doppler:
auth:
secretRef:
dopplerToken:
name: doppler-token-auth-api
key: dopplerTokenapiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: doppler-auth-api
spec:
provider:
doppler:
auth:
secretRef:
dopplerToken:
name: doppler-token-auth-api
key: dopplerToken
project: your-project-name
config: your-config-nameIn case of a
ClusterSecretStore, be sure to setnamespaceinsecretRef.dopplerToken.
Use Cases
The Doppler provider allows for a wide range of use cases:
Let's explore each use case using a fictional auth-api Doppler project.
You specify the project and config being fetched for an ExternalSecret in the SecretStore spec (see the Service Account Token example above).
1. Fetch
To sync one or more individual secrets:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: auth-api-db-url
spec:
secretStoreRef:
kind: SecretStore
name: doppler-auth-api
target:
name: auth-api-db-url
data:
- secretKey: DB_URL
remoteRef:
key: DB_URL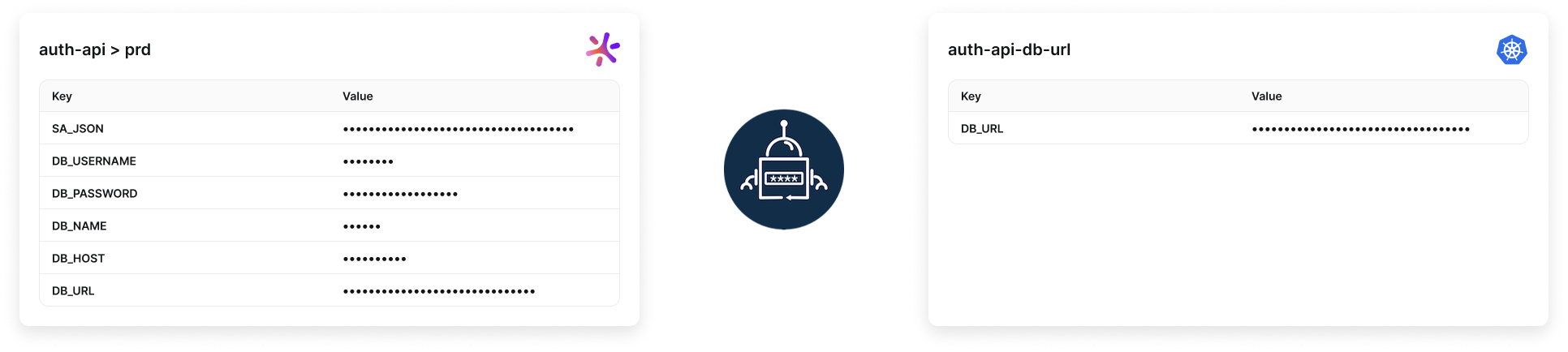
2. Fetch all
To sync every secret from a config:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: auth-api-all
spec:
secretStoreRef:
kind: SecretStore
name: doppler-auth-api
target:
name: auth-api-all
dataFrom:
- find:
name:
regexp: .*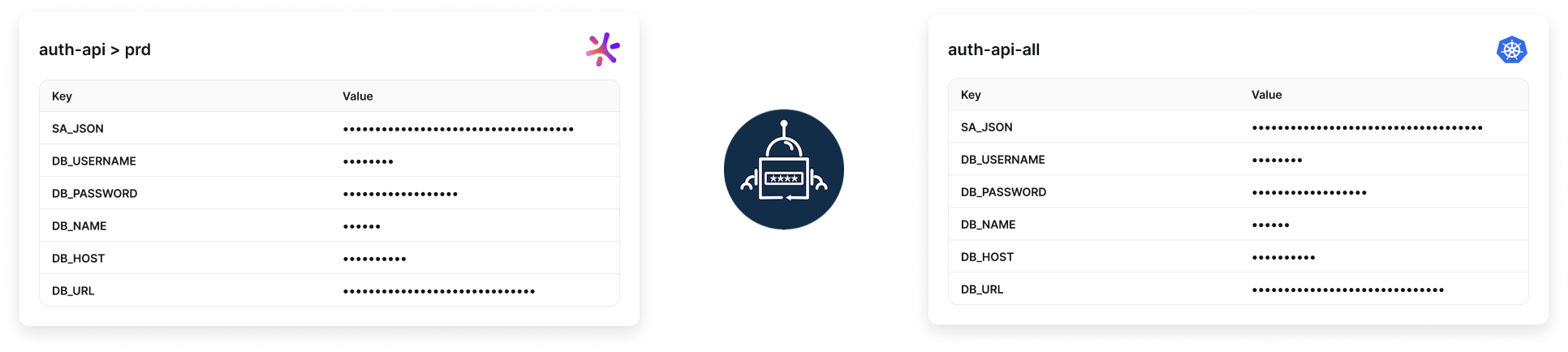
3. Filter
To filter secrets by path (path prefix), name (regular expression) or a combination of both:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: auth-api-db
spec:
secretStoreRef:
kind: SecretStore
name: doppler-auth-api
target:
name: auth-api-db
dataFrom:
- find:
path: DB_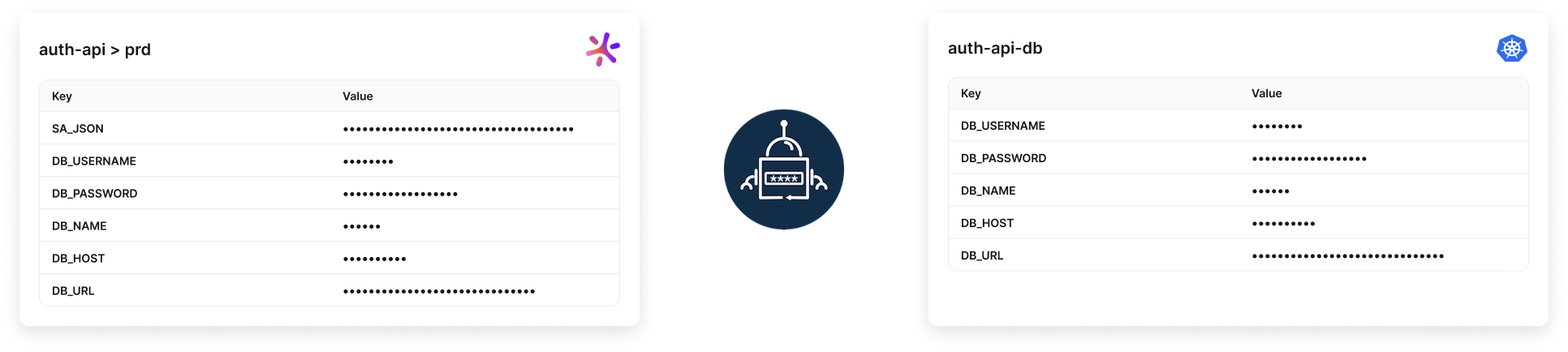
4. JSON secret
To parse a JSON secret to its key-value pairs:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: auth-api-sa-json
spec:
secretStoreRef:
kind: SecretStore
name: doppler-auth-api
target:
name: auth-api-sa-json
dataFrom:
- extract:
key: SA_JSON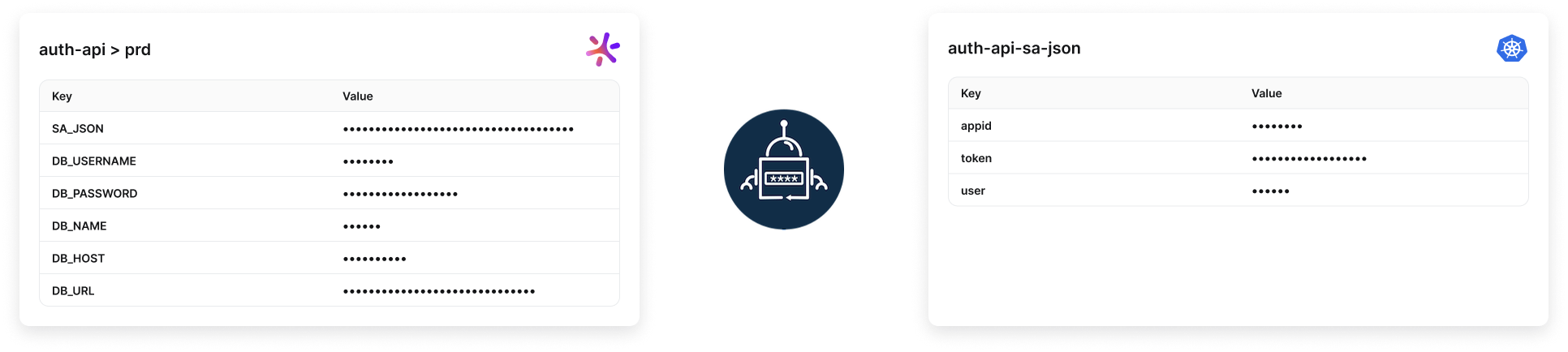
5. Name transformer
Name transformers format keys from Doppler's UPPER_SNAKE_CASE to one of the following alternatives:
- upper-camel
- camel
- lower-snake
- tf-var
- dotnet-env
- lower-kebab
Name transformers require a specifically configured SecretStore:
apiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: doppler-auth-api-dotnet-env
spec:
provider:
doppler:
auth:
secretRef:
dopplerToken:
name: doppler-token-auth-api
nameTransformer: dotnet-envapiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: doppler-auth-api-dotnet-env
spec:
provider:
doppler:
auth:
secretRef:
dopplerToken:
name: doppler-token-auth-api
project: your-project-name
config: your-config-name
nameTransformer: dotnet-envThen an ExternalSecret referencing the SecretStore:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: doppler-auth-api-dotnet-env
spec:
secretStoreRef:
kind: SecretStore
name: doppler-auth-api-dotnet-env
target:
name: doppler-auth-api-dotnet-env
creationPolicy: Owner
dataFrom:
- find:
name:
regexp: .*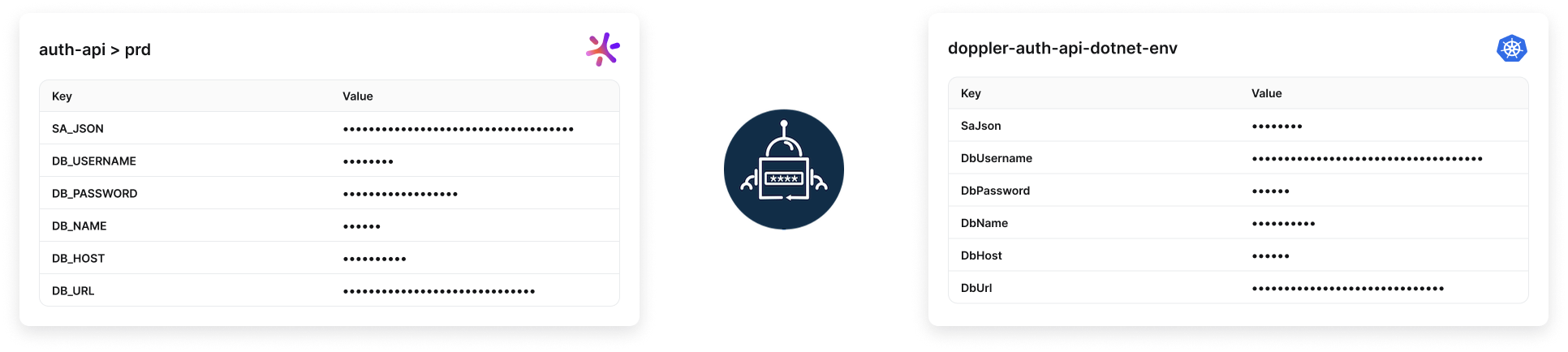
6. Download
A single DOPPLER_SECRETS_FILE key is set where the value is the secrets downloaded in one of the following formats:
- json
- dotnet-json
- env
- env-no-quotes
- yaml
Downloading secrets requires a specifically configured SecretStore:
apiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: doppler-auth-api-json-file
spec:
provider:
doppler:
auth:
secretRef:
dopplerToken:
name: doppler-token-auth-api
key: dopplerToken
format: jsonapiVersion: external-secrets.io/v1beta1
kind: SecretStore
metadata:
name: doppler-auth-api-json-file
spec:
provider:
doppler:
auth:
secretRef:
dopplerToken:
name: doppler-token-auth-api
key: dopplerToken
project: your-project-name
config: your-config-name
format: jsonThen an ExternalSecret referencing the SecretStore:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: auth-api-json-file
spec:
secretStoreRef:
kind: SecretStore
name: doppler-auth-api-json-file
target:
name: auth-api-json-file
dataFrom:
- find:
path: DOPPLER_SECRETS_FILE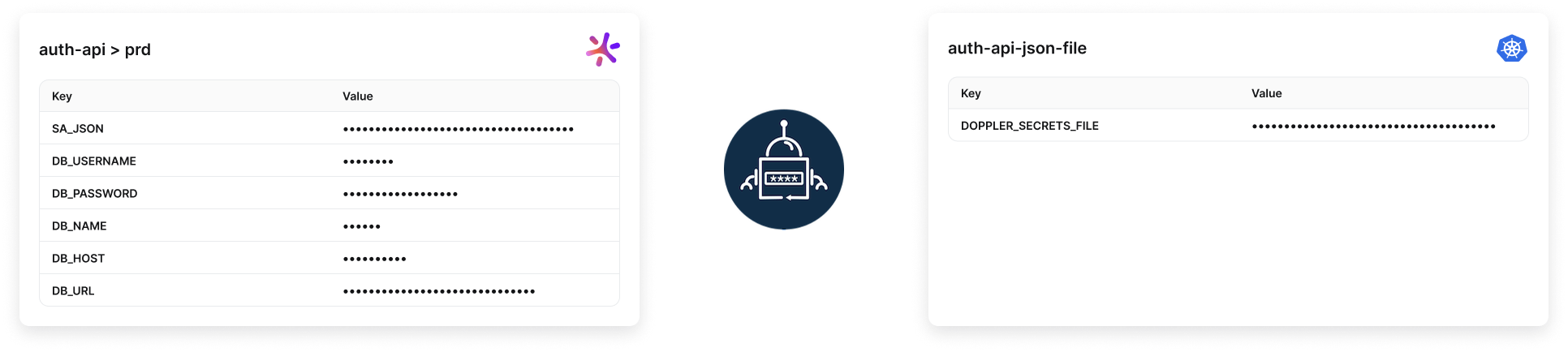
Updated 5 months ago
