Doppler Kubernetes Operator
Kubernetes secrets sync automation with deployment auto-reload on secrets change.
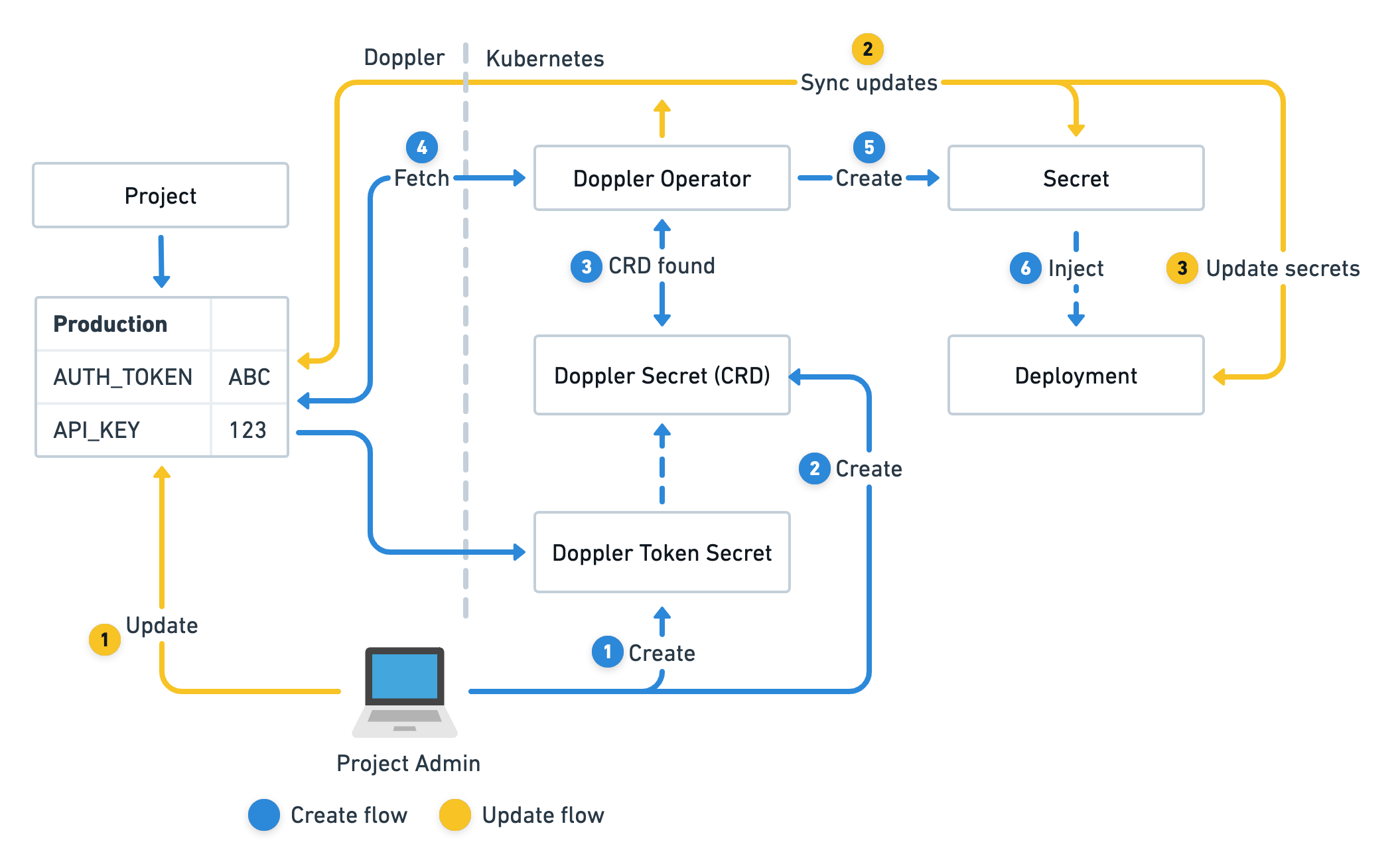
The Doppler Secrets Operator is a background service that syncs secrets to Kubernetes with automatic deployment updates to ensure applications always have the latest version of secrets.
More specifically, the operator is a controller deployed inside your Kubernetes cluster within its own dedicated doppler-operator-system namespace so RBAC policies can tightly restrict access.
The operator uses DopplerSecret custom resources which define what Doppler configs to sync, the name of the associated Kubernetes secret the operator will manage as well what namespace it should be created in.
The operator is then solely responsible for continuously syncing secret updates in Doppler to its managed Kubernetes secrets and can optionally automatically reload any deployments that reference a managed secret.
Updated 4 months ago
