Service Account Identities (OIDC)
Requires an upgraded subscriptionThis feature is available with our Team and Enterprise plans. View our plans or book a demo for more details.
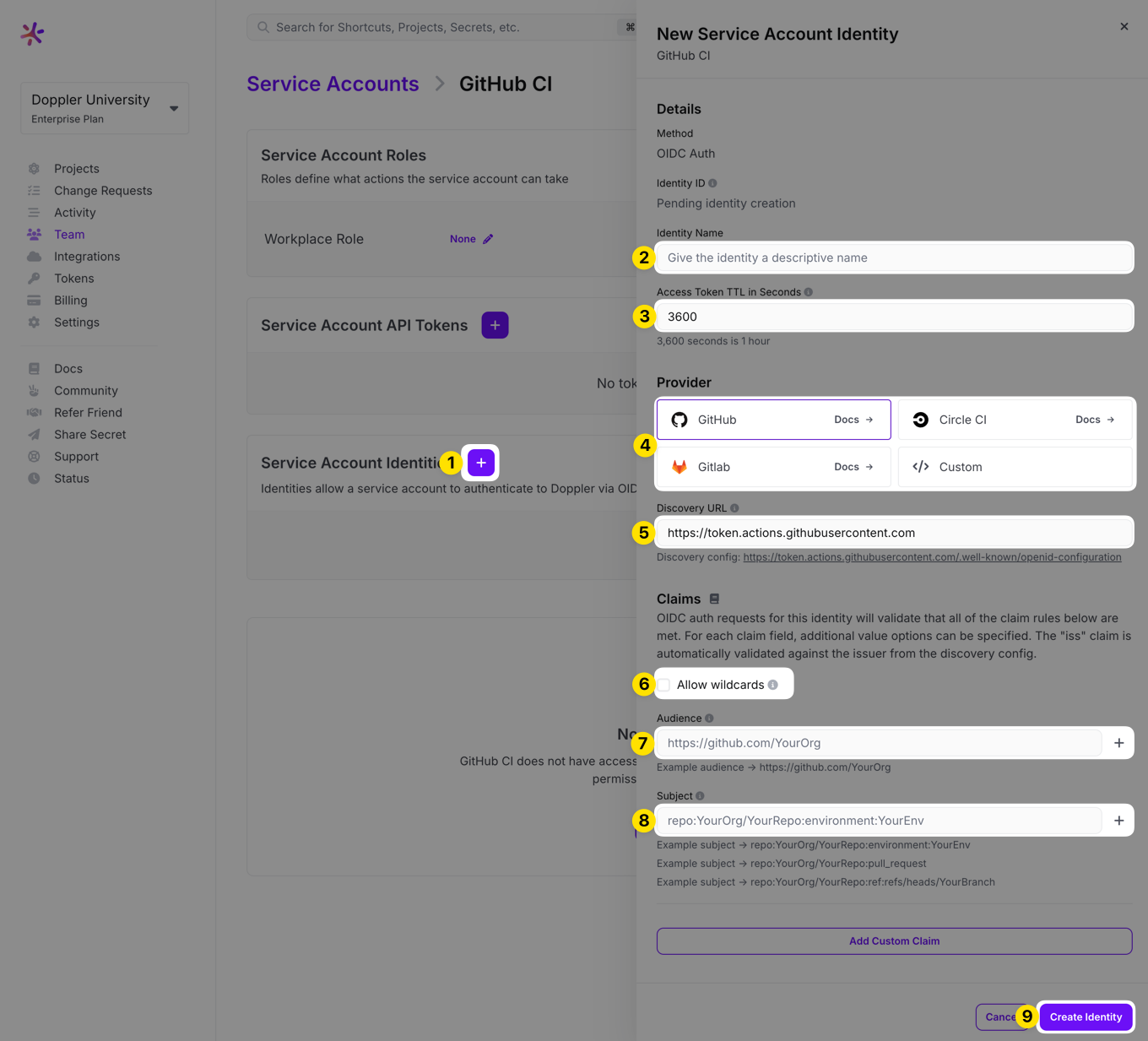
Identities allow a service account to authenticate to Doppler via OIDC without using a static API token. Any tool that can generate OIDC tokens (e.g., CI tools like GitHub or GitLab) is compatible with Doppler.
Use the service account detail page to configure an identity. Then, utilize the Doppler CLI, API, or GitHub Secrets Fetch Action in order to authenticate via identity auth using an OIDC token generated by your CI tool.
Configure the identity
- Visit the service account detail page in Doppler
- Click "new identity" in the Service Account Identities section
- Select your provider (or provide a custom Discovery URL - you can verify the discovery data by clicking on the generated link below the field)
- Configure the claims that Doppler will validate in the token signed by your OIDC provider. OIDC auth requests for this identity will validate that all of the claim rules are met.
- Avoid wildcards if possible as simpler/exact match rules are simplest to configure and reason about.
- Audience and subject claims are required. Additional custom claims can be added as desired (e.g., GitLab provides a custom claim
environment). - For each claim field, additional value options can be specified. One option must match for every configured claim in order for an identity auth request to succeed.
- Examples of the formats provided for your provider are displayed below the inputs. For example, GitHub has multiple formats for Subject depending on the context (e.g., environment vs pull request). The docs links in the provider section provides further detail.
- After creating the identity, the identity's ID will be displayed. This is a configuration value, not a secret, that will be utilized during identity authentication.
Authentication with an identity
Option 1: Kubernetes via the Doppler Kubernetes Operator
- Configure your Kubernetes cluster and operator as described in the Kubernetes Operator OIDC Setup.
Option 2: GitHub via the Secrets Fetch Action
- Configure your GitHub Action as noted in the Secrets Fetch Action README .
Option 3: Any OIDC provider via the Doppler CLI
These steps typically occur inside the context of a third party OIDC provider job (e.g., inside a GitHub Action workflow or CircleCI job).
- Retrieve an OIDC token from your OIDC provider (e.g.,
$CIRCLE_OIDC_TOKEN_V2or GitHub'sgetIDToken()). See the providers OIDC documentation for details (direct links provided from the Service Account Identity edit drawer). - Authenticate via the OIDC token string from your CI provider:
doppler oidc login --scope=. --identity=00000000-0000-0000-0000-000000000000 --token=$CIRCLE_OIDC_TOKEN_V2 - Use the CLI as desired, for example:
doppler secrets --project example --config dev - (Optional) The short lived API token can be revoked when you are finished. This is not necessary, as the tokens expire quickly and you should not persist them.
doppler oidc logout --scope=.
Option 4: Any OIDC provider via the Doppler API
- Retrieve an OIDC token from your OIDC provider (e.g.,
$CIRCLE_OIDC_TOKEN_V2or GitHub'sgetIDToken()). See the providers OIDC documentation for details (direct links provided from the Service Account Identity edit drawer). - Make a POST request to
https://api.doppler.com/v3/auth/oidcwith JSON body with the propertiesidentity(Identity ID from the Doppler Dashboard) andtoken(the OIDC token string from your CI provider). - The response JSON contains
tokenwhich is a short lived API token that can be used as a Bearer token when using the Doppler API. The response also contains the expiration date/timeexpires_at. - (Optional) The short lived API token can be revoked just like other Doppler API tokens when you are finished. This is not typically necessary, as the tokens expire quickly and you should not persist them.
Updated 4 months ago
