Jenkins
Learn how to integrate Doppler into your Jenkins CI jobs.
This guide will show you how to use Doppler to provide secrets to CI jobs in Jenkins.
Prerequisites
- You have created a project in Doppler
- You have a working Jenkins installation with the credentials plugin installed.
- You have the Doppler CLI installed on your Jenkins executor nodes or container images.
Select Doppler Config
Using Doppler to manage your CI secrets requires only a single DOPPLER_TOKEN variable to be stored in Jenkins, which is used by the Doppler CLI to fetch the latest version of your secrets during each job run.
We recommend you first migrate any existing CI job variables to Doppler prior to making any changes in Jenkins. Most customers opt to organize their CI variables using a Branch Config under the Staging environment. You could also create a custom environment named Jenkins for this as well though and forego using a branch config.
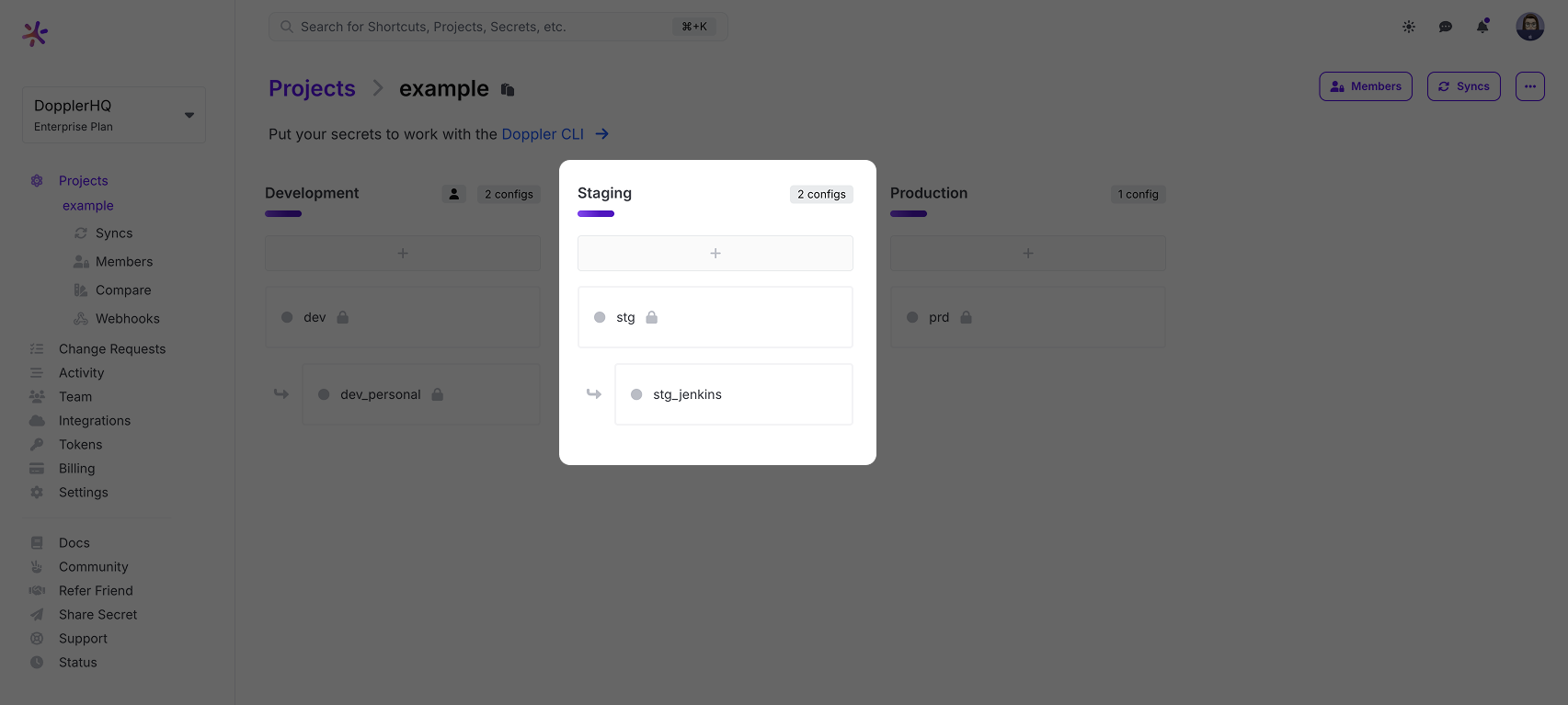
Add Doppler Service Token
After creating a Branch Config, create a Service Token for Jenkins to use to access the secrets in Doppler. Once you have the token, browse to Manage Jenkins > Manage Credentials in your Jenkins installation.
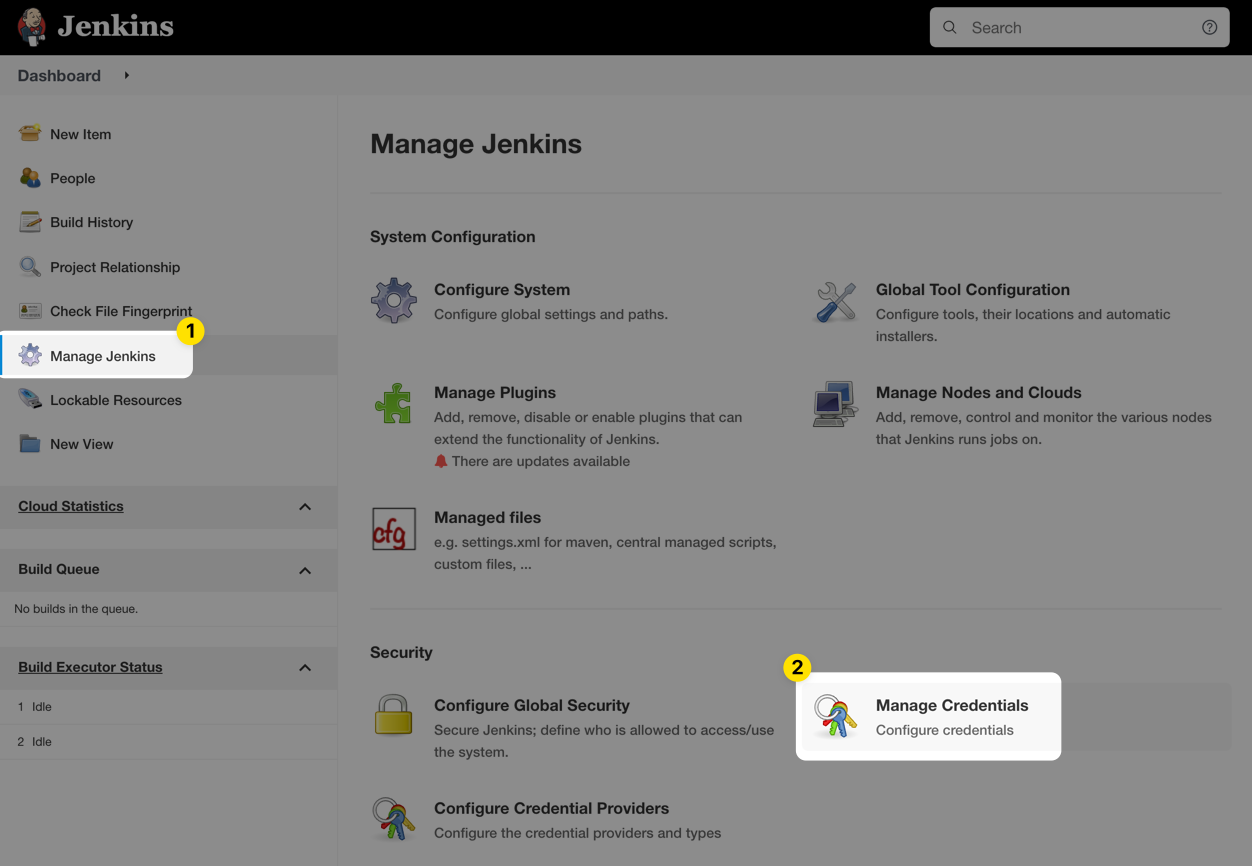
Click on the credential store you want to store the Doppler service token in. In this case, we're using the default Jenkins global store. Each of your projects will have a different DOPPLER_TOKEN though, so it may make sense to spread these out into separate credential domains depending upon your use case.
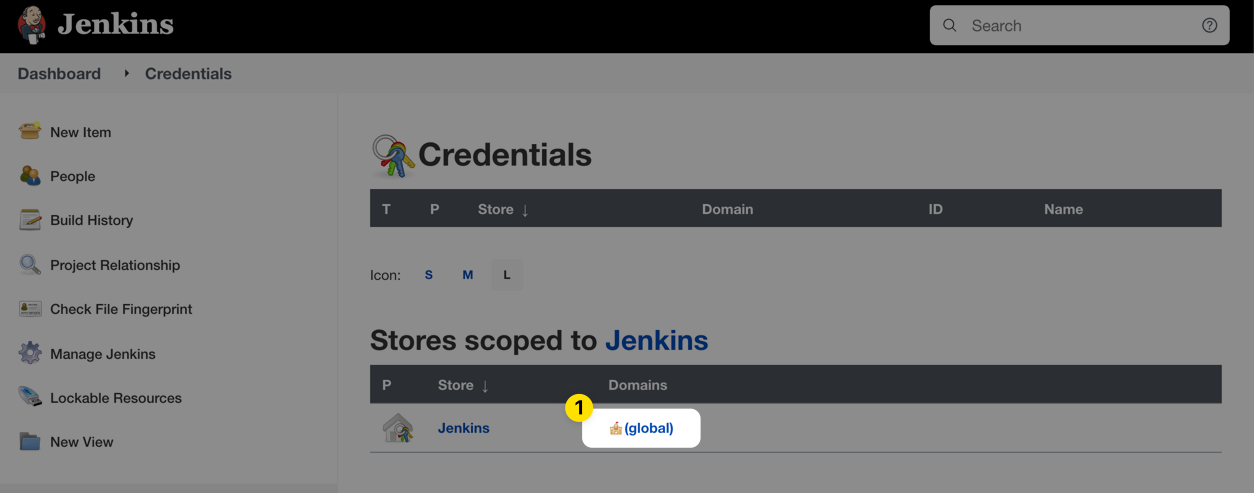
Click Add Credential:
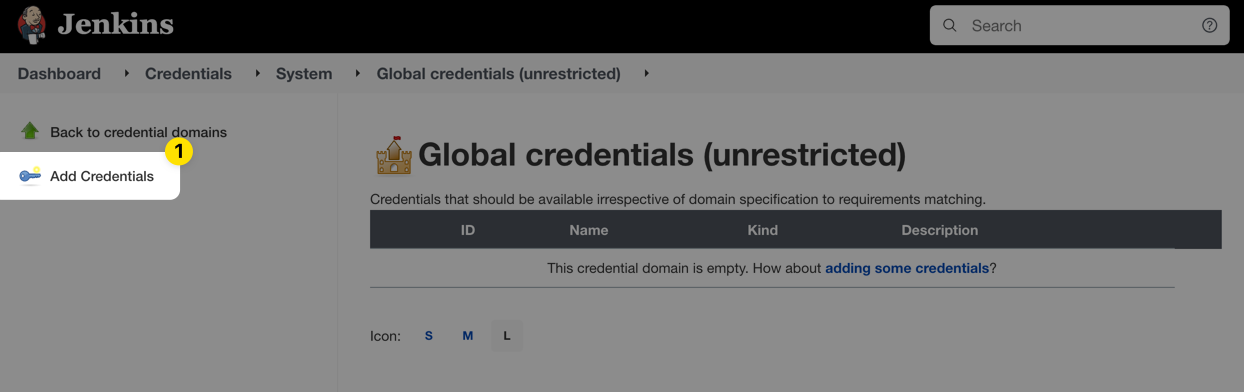
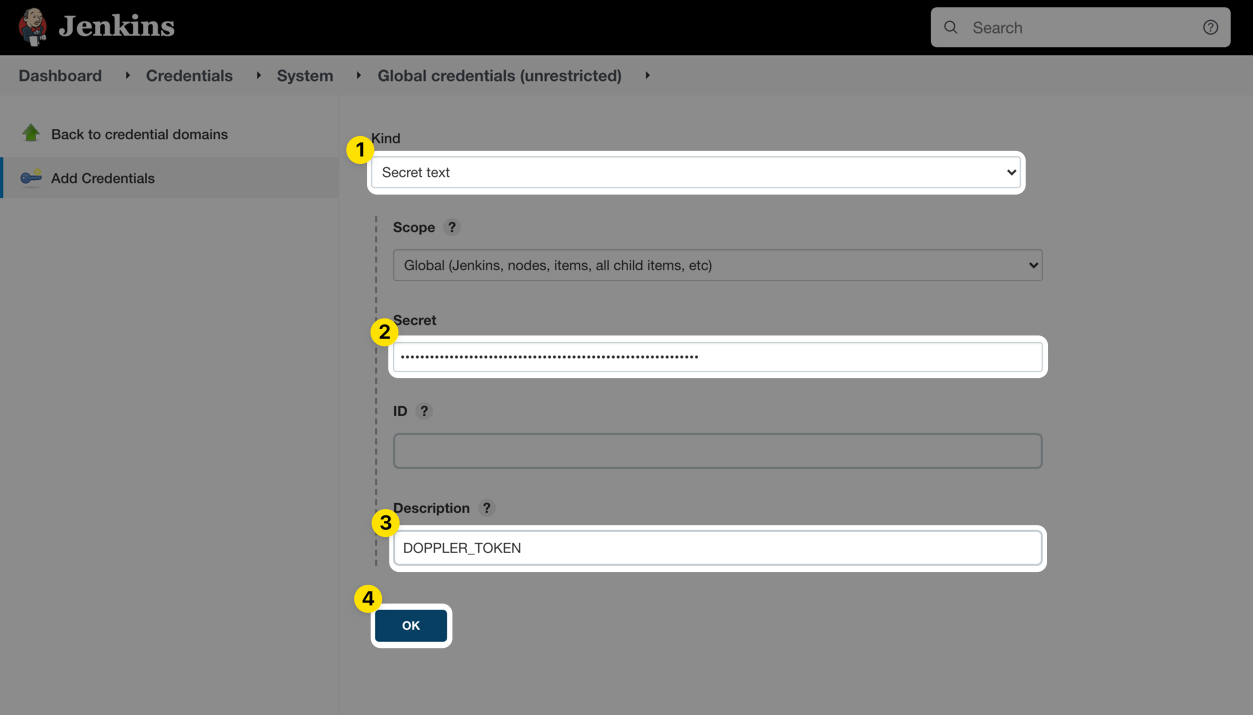
Choose Secret text from the Kind dropdown menu, paste the Doppler service token into the Secret field, enter DOPPLER_TOKEN into the Description field, and then click OK.
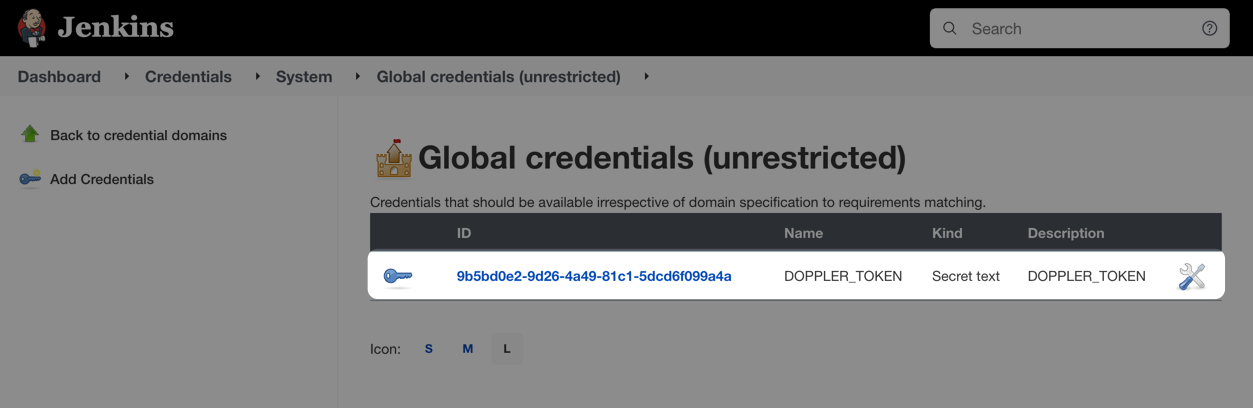
When you're done, you should have a credential similar to this showing:
Usage in a Freestyle Project
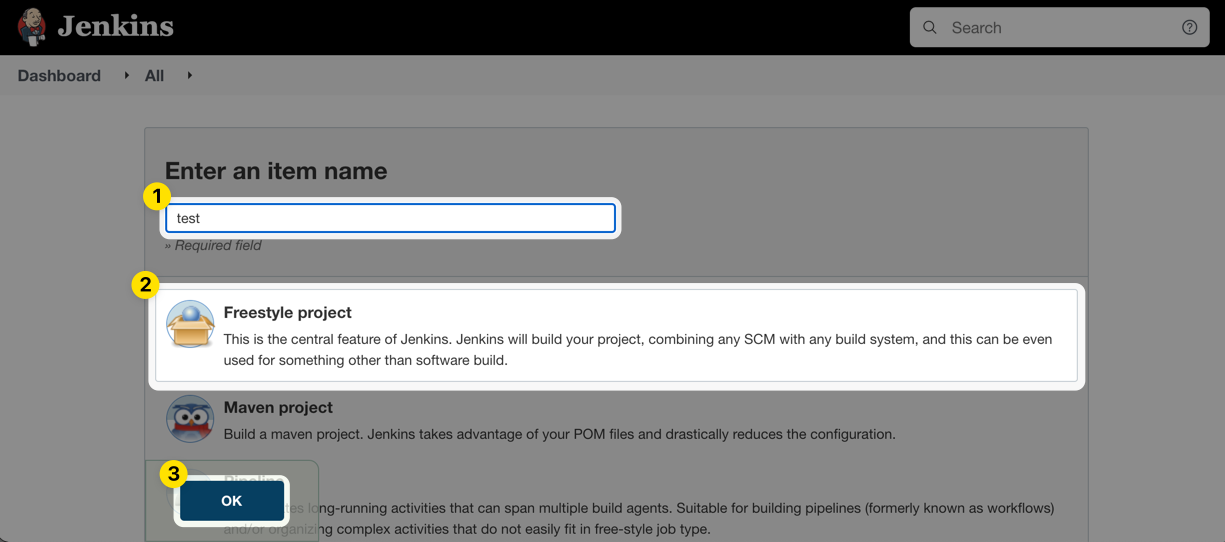
To use Doppler in a Freestyle Project job, you'll need to expose the credential you created above in an environment variable. First, click New Item from the dashboard navigation sidebar:

Enter the name of the job, choose the Freestyle project option, and click OK.
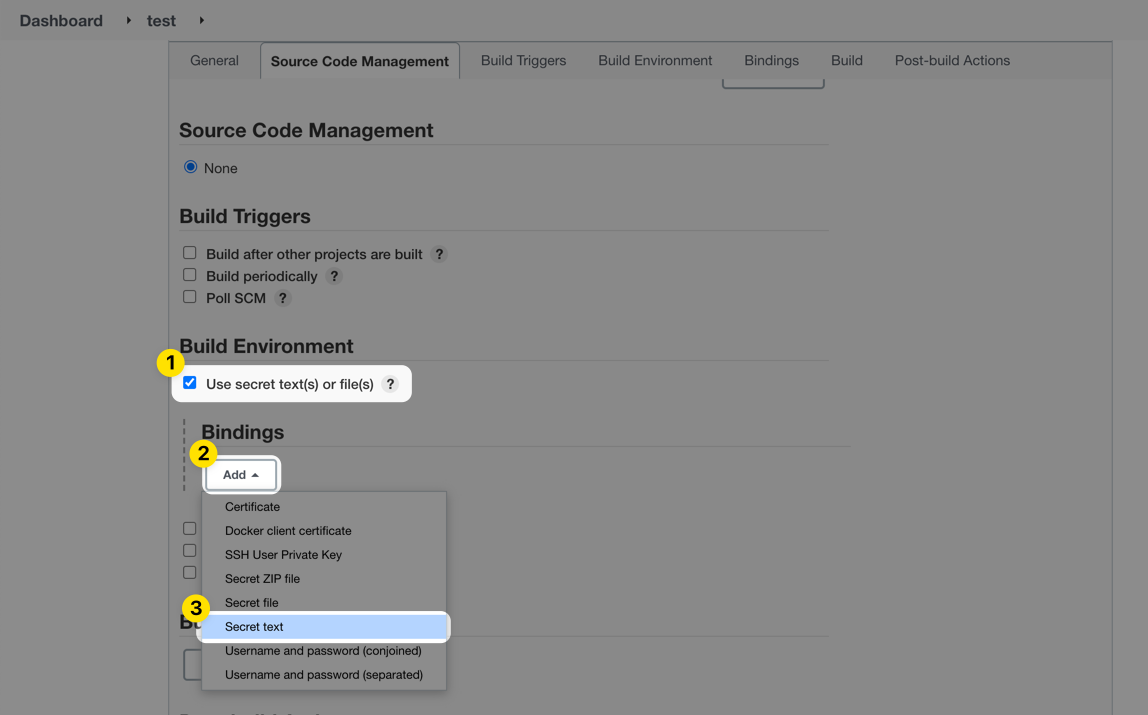
Scroll down to the Build Environment section and enable the Use secret text(s) or file(s) option. Then click Add under Bindings and choose Secret text from the dropdown menu.
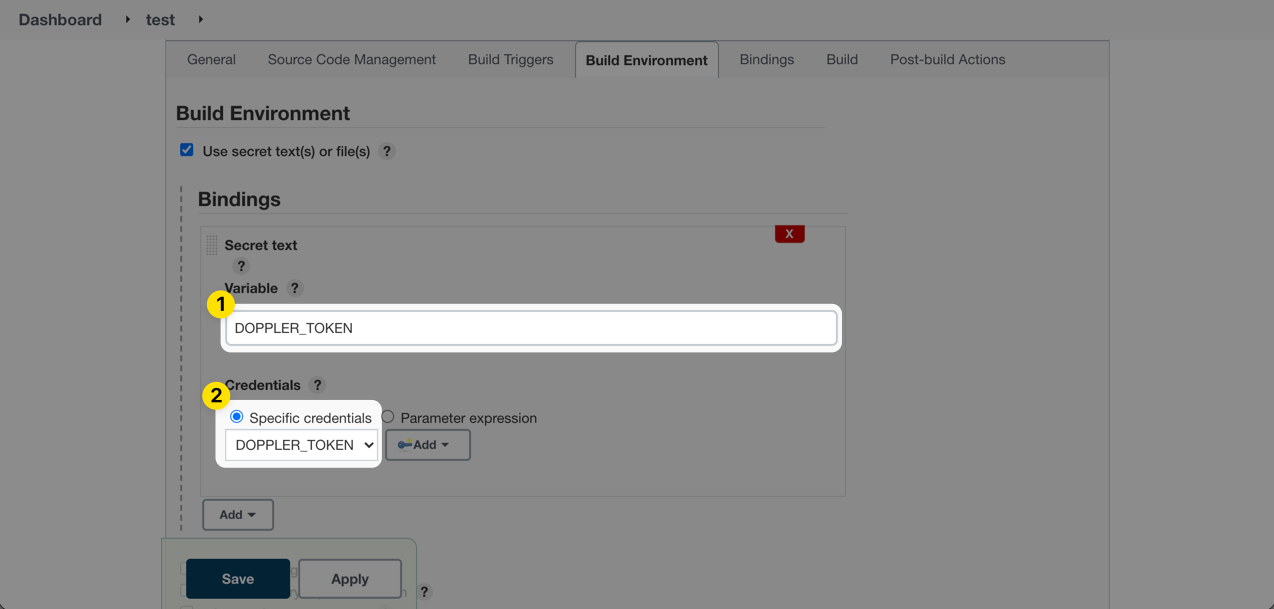
Enter DOPPLER_TOKEN in the Variable field, select the Specific credentials option from the Credentials section and choose DOPPLER_TOKEN from the dropdown menu.
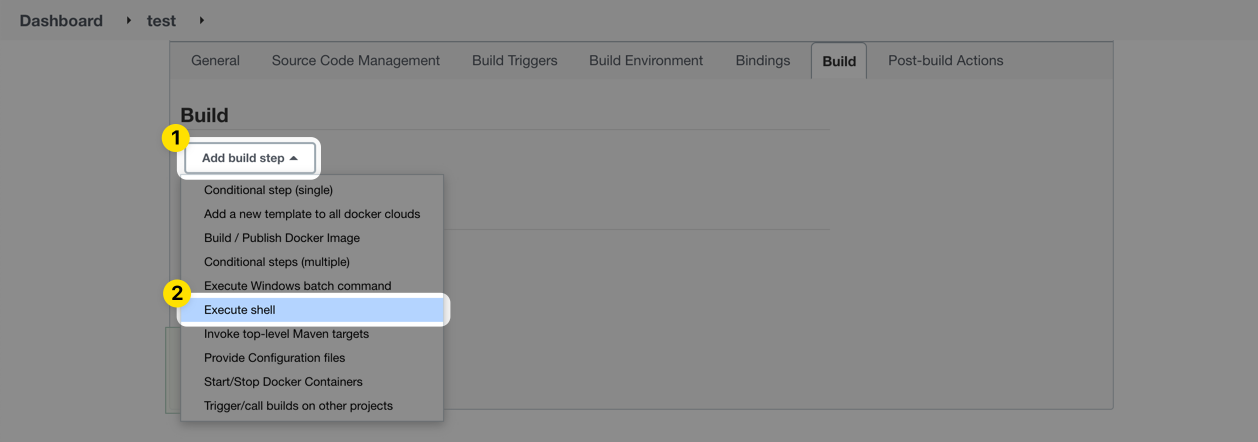
Scroll down to the Build section and choose Execute shell from the Add build step menu.
In the command field, enter the following and click Save:
doppler run -- printenv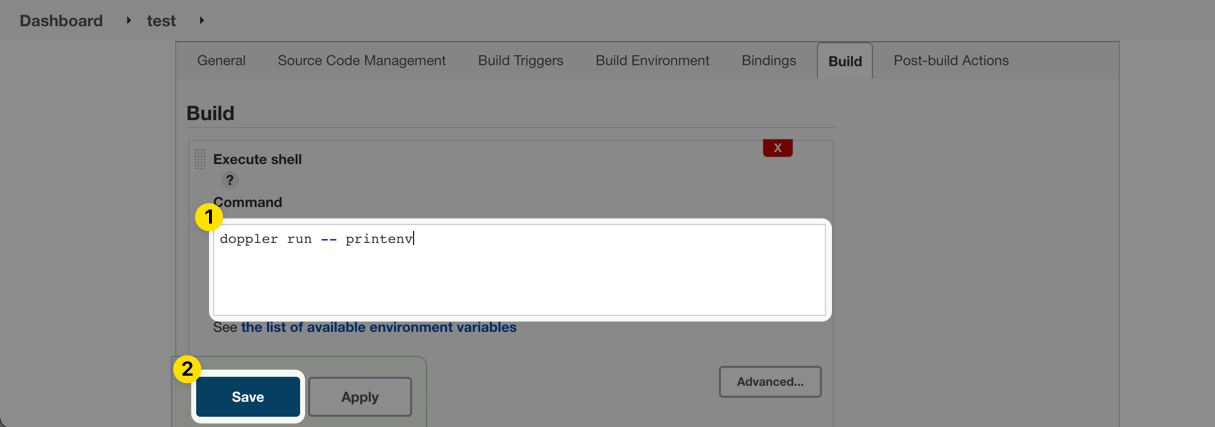
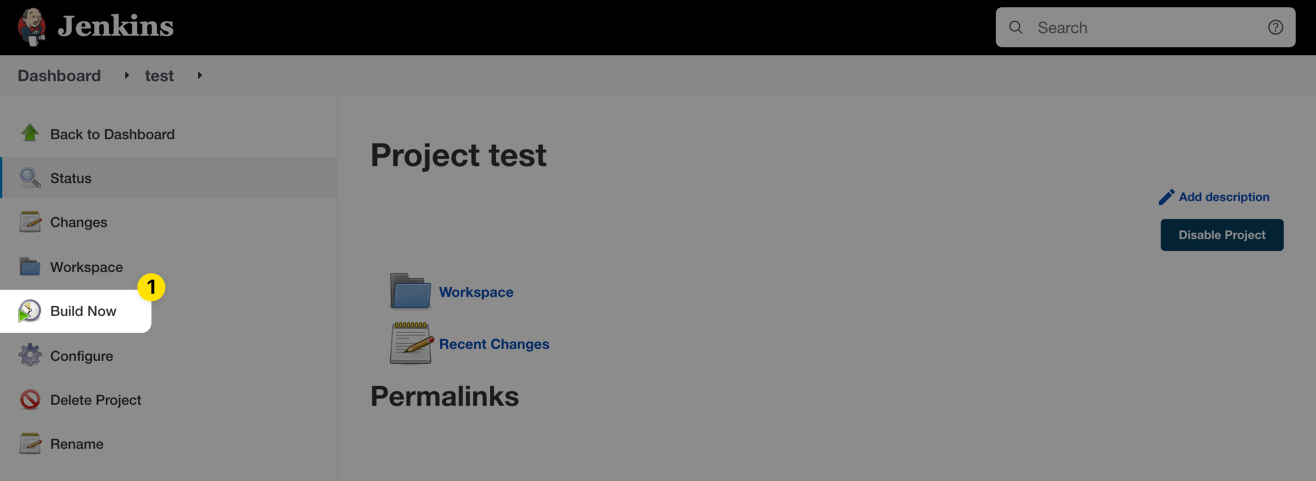
Finally, click Build Now from the navigation sidebar to test your new job.
Usage in a Pipeline
To use Doppler in a Freestyle Project job, you'll need to expose the credential you created above in an environment variable. First, click New Item from the dashboard navigation sidebar:

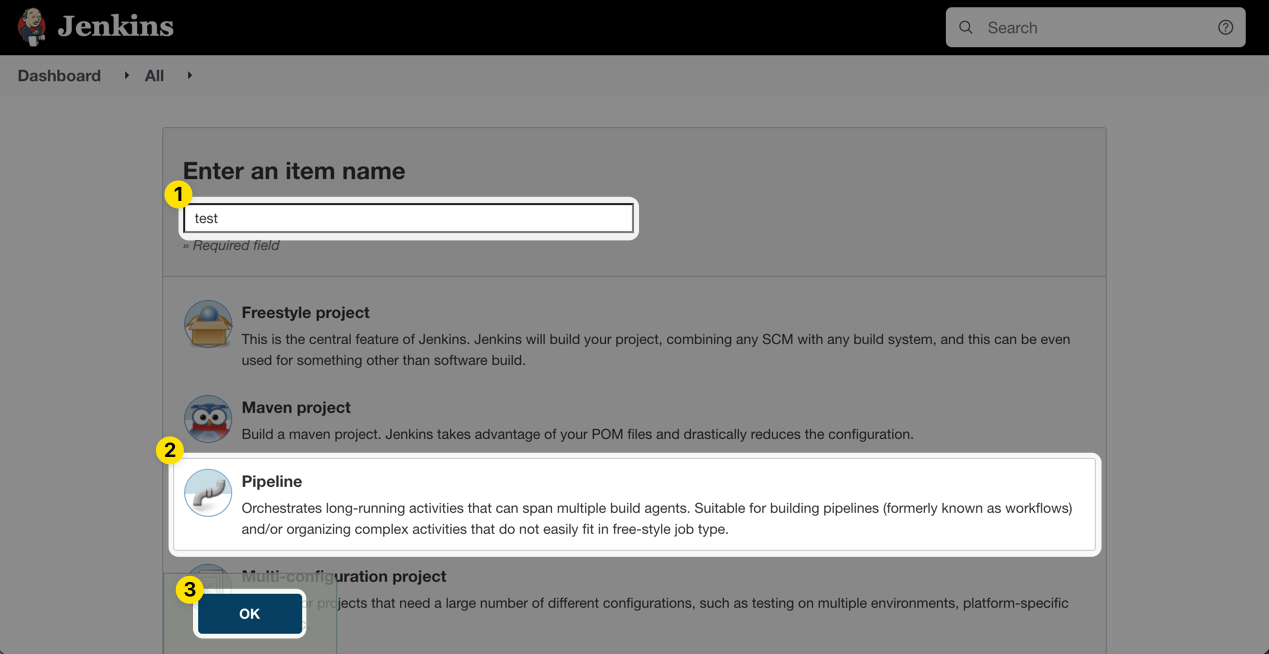
Enter the name of the job, choose the Pipeline option, and click OK.
Scroll down to the Pipeline section, paste the following into the Script field, and then click Save.
pipeline {
agent any
environment {
DOPPLER_TOKEN = credentials('DOPPLER_TOKEN')
}
stages {
stage('Run Doppler') {
steps {
sh("doppler secrets --only-names")
// doesn't work
// sh("docker run --rm test-container doppler secrets")
// works
// sh("docker run -e DOPPLER_TOKEN=${DOPPLER_TOKEN} --rm test-container doppler secrets")
// doesn't work
// sh("docker-compose up -d")
// works
// sh("DOPPLER_TOKEN=${DOPPLER_TOKEN} docker-compose up -d")
}
}
}
}This is a very basic sample that you can work from. Jenkins injects the DOPPLER_TOKEN environment variable defined in the pipeline into the shell the commands execute with, but there are some situations where that won't pass through properly – notably if you're executing docker containers on the executor machine. The examples above should give you some idea for how that will work.
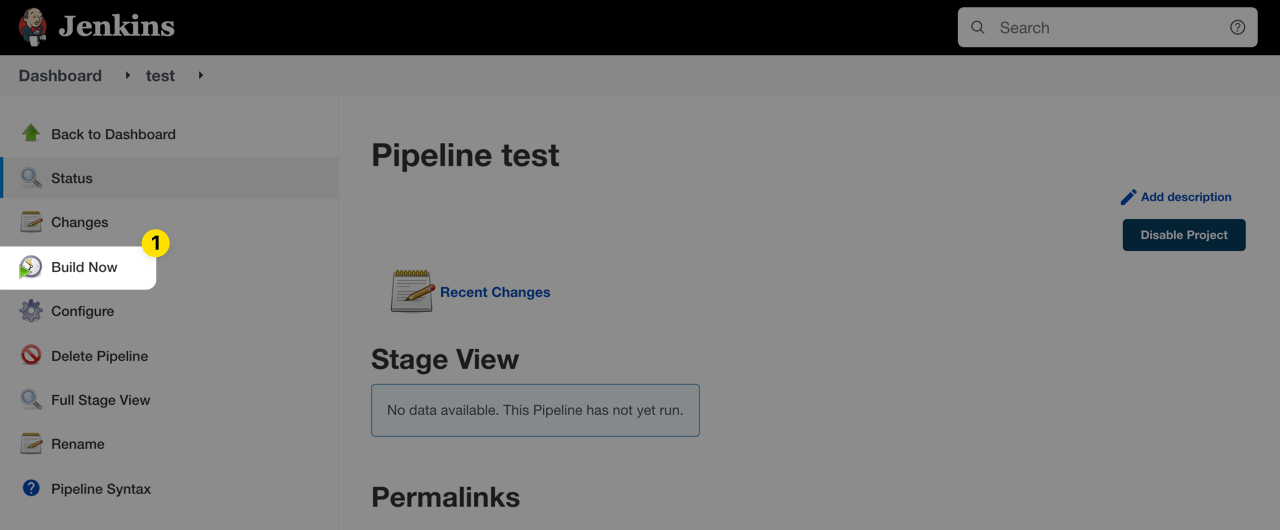
Finally, click Build Now from the navigation sidebar to test your new job.
Updated 5 months ago
