Splunk
This guide will show you how to send Doppler Activity Logs to Splunk.
Requires an upgraded subscriptionThis feature is exclusive to our Enterprise Plan. Book a demo to see it in action.
Prerequisites
- Ability to add a new Splunk Event Collector
- Paid Splunk account
- Doppler Enterprise plan
If you're testing with the Splunk Cloud free trial, you won't be able to use this because they use a self-signed SSL certificate with free trials, which fails our setup validations.
Create a new Event Collector
Within Splunk, select Data Inputs from the Settings dropdown
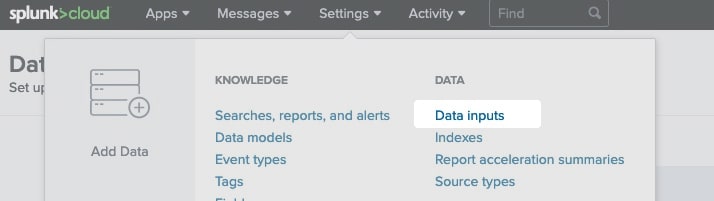
In the HTTP Event Collector row, click Add new
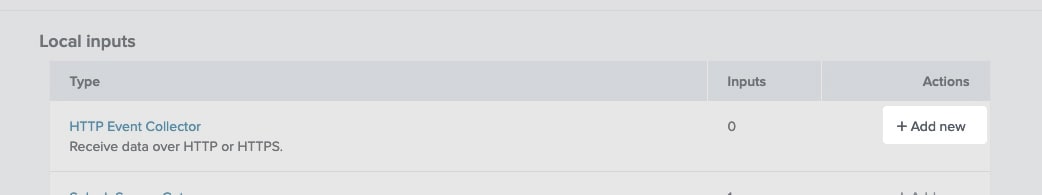
Give your Event Collector Token a name at minimum
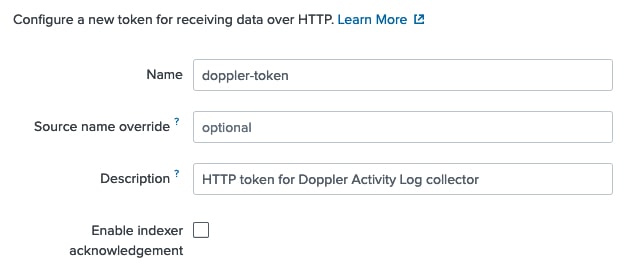
Doppler sends Activity Logs as a JSON payload. In the Source Type, choose Select and then search for and select _json. As well, select the Index you want Doppler Activity Log data to land in
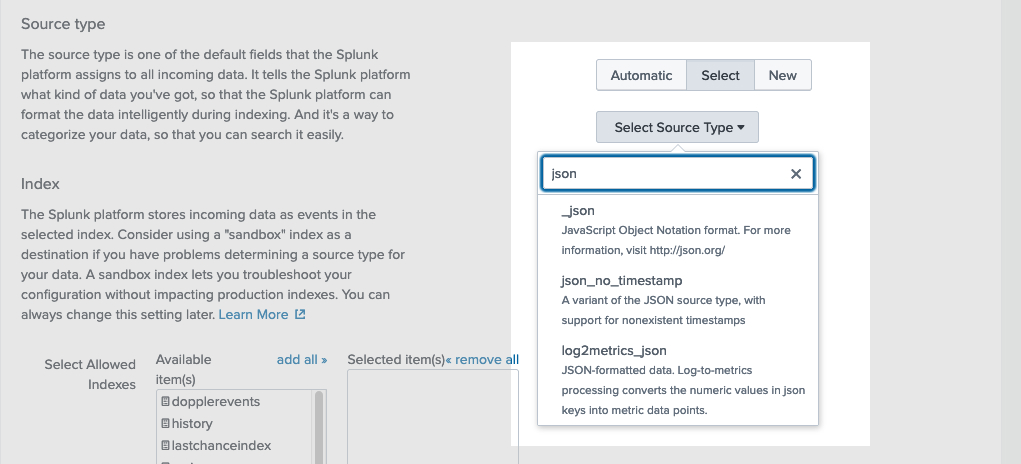
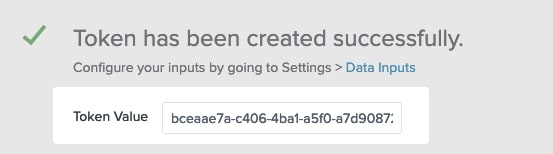
On the next screen, review your configuration. When you've confirmed your selections, hit submit. On the confirmation page, highlight and copy the Token that's shown. You'll enter that in Doppler in a moment.
Head on over to Doppler and visit the Settings page. Scroll down until you see the Services section. You'll find two inputs for Splunk. One for the Token you just generated and another for your HTTP endpoint.
Go ahead and enter your token. For the HTTPS endpoint, we recommend viewing this link for an in-depth explanation on constructing your URL. Given that we're using a JSON payload, please ensure your URL ends with /services/collector/event. Construction this URL can be a bit tricky so if you run into issues, don't hesitate to reach out to [email protected] with any questions
Updated 4 months ago
