Secret Visibility
Learn about secret visibility – how it works and how to use it!
While we secure every value we receive in the same manner, we recognize that organizations store many types of data in Doppler, ranging from non-sensitive values, such as database ports, to highly sensitive values, like database passwords. The difference in sensitivity means organizations often want to interact with the values differently. For instance, database passwords may not be intended to be viewable once they're saved, while a port can always be viewed without requiring an action to reveal it. That's where secret visibility comes in.
Overview
| Visibility | Dashboard Retrieval | Programmatic Retrieval | Integration Syncs |
|---|---|---|---|
| Unmasked | Always displayed - does not require an intention to reveal | Retrievable via any token type | Supported |
| Masked | Masked - **** - by default. Value can be revealed by clicking on it | Retrievable via any token type | Supported |
| Restricted | Not viewable in the dashboard after it is saved | Retrievable only via non-user tokens (e.g. a service token) | Supported |
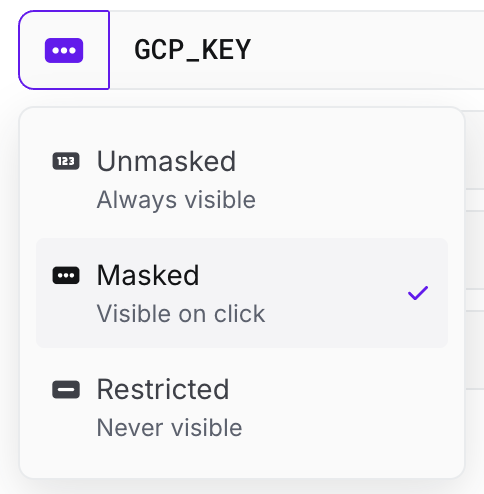
Unmasked Visibility
Unmasked values are always visible in the dashboard - their value is never masked or hidden in any retrieval mechanism.
Masked Visibility
Masked values are not displayed in the dashboard until there is an intent performed by the user to reveal the value - typically a mouse click.
Restricted Visibility
Once a value is set to Restricted, you will never be able to view it in the dashboard again.
Restricted values are not visible in the dashboard once they are saved; as well, they are only visible when retrieved programmatically if the authentication method is a service token. The value is not returned if the authentication method is tied to a user identity (like a personal token or CLI token). Restricted values are also supported in integration syncs.
Users who are able to generate non-user tokens (e.g. service tokens, service account tokens) will be able to use those tokens to reveal restricted secrets via the CLI or API. This includes the case where a user is able to create a reference to a restricted secret in a different config where they cannot generate tokens.
CLI
CLI behavior varies depending on the version of the Doppler CLI that you're using. We recommend using v3.58.0 or higher.
- All CLI versions when using a personal token or CLI token
- Will return a
403when usingdoppler secrets downloadordoppler run
- Will return a
- CLI version
v3.58.0, or newer, when using a personal token or CLI token- Restricted secret values will appear as
[RESTRICTED]in the printed table - Restricted secret values will be
nullwhen outputting json (via the--jsonflag, withdoppler secretsordoppler secrets get)
- Restricted secret values will appear as
- CLI version
v3.57.1, or older, when using a personal token or CLI token- Restricted secret values will appear as an empty cell in the printed table
- Restricted secret values will be an empty string (
"") when outputting json (via the--jsonflag, withdoppler secretsordoppler secrets get)
Empty Values
Empty values will be displayed as 'empty', regardless of the visibility. This allows you to distinguish between restricted secrets with and without a value.
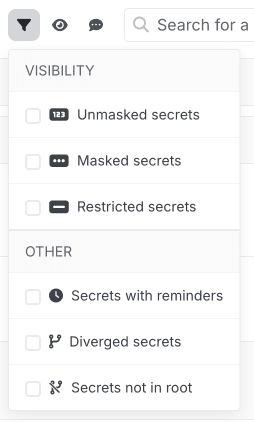
Visibility Filters
At the top of each config, clicking Filter allows you to filter by specific visibility.
Visibility Properties in the API
Although visibility is set per-secret, using references may further restrict the computed visibility of a given secret.
For example, consider two secrets, S1 and S2, where S1 is a restricted secret and S2 is a masked secret whose value is ${S1}. In this case, the "raw" visibility of S2 is masked. However, when the reference is resolved, the "computed" visibility of S2 must be restricted since it references a restricted secret.
These two properties are surfaced as rawVisibility and computedVisibility in the API.
Changing a Secret's Visibility
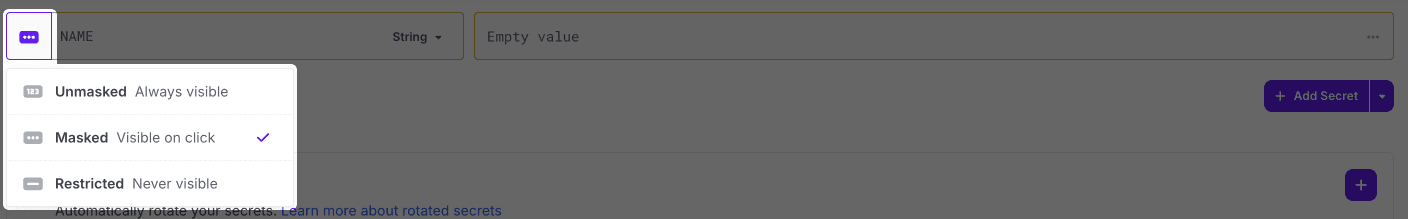
A secret's visibility can be adjusted by clicking the visibility icon next to the secret's name.
- An unmasked or masked value can be set to any visibility at any time
- A restricted value can only changed to a more permissive visbility (masked or unmasked) when also changing its value. This limitation is to prevent leaking the restricted value
Cascading Changes
Learn more about how the visibility of a secret is handled when cascading changes to other environments on save in our Secrets page.
Updated 4 months ago
