AWS Secrets Rotation
Doppler rotates secrets that reside within AWS infrastructure by utilizing AWS Lambda as a proxy. There's no need to expose your services to the internet or grant Doppler access to your services.
Requirements
Requires an upgraded subscriptionThis feature is exclusive to our Enterprise Plan. Book a demo to see it in action.
- Understand the Doppler rotation methodology
- AWS Account
- Ability to create IAM roles and Policies
- Ability to create Lambda functions
- Ability to create AWS Gateway Endpoints
Overview
To rotate secrets for any system within AWS, Doppler invokes a Lambda function that you create and own within your cloud account using a minimally scoped IAM role. Each Lambda function is open source, signed, and hosted in S3. Each Lambda invocation payload is signed and verified using our public key, which is also hosted in S3.
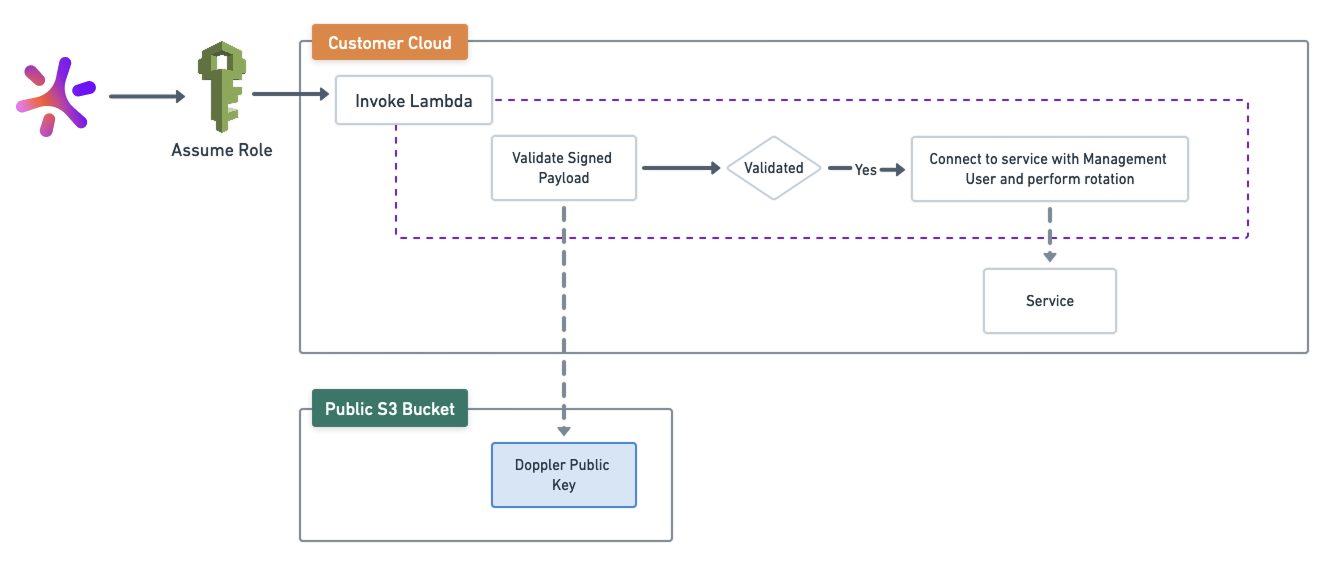
Primitives
Each AWS rotated secret, regardless of the type, utilizes the same AWS primitives.
| Primitive | Use |
|---|---|
| Lambda | Performs the secret rotation |
| Lambda Execution Role & Policy | Authorization context the Lambda is executed in |
| Assumed IAM Role & Policy | Role Doppler assumes into your AWS account with in order to execute the Lambda function |
| Doppler Code Signing Profile | Doppler signing profile which validates the authenticity of the Lambda code |
| Doppler Public Key | Used to validate the payload passed to the Lambda function |
| S3 Gateway Endpoint | Connection between the Lambda function and the S3-hosted Doppler public key. Required when a Lambda function is in a VPC. |
For each primitive, there may be customization required depending on your architecture - e.g. VPC peering. As well, the service you are rotating may need its own configuration, which will be covered in its own dedicated doc.
Supported Services
- MySQL (RDS or self-hosted)
- Postgres (RDS or self-hosted)
- MS SQL Server (RDS or self-hosted)
Rotated Secret Creation
- Navigate to the secrets config that the rotated secret will reside in
- Go to the Secrets tab
- Select Add Rotated Secret
- Select the service you'd like to rotate and then select AWS
Lambda Setup
Executor Role
The Lambda executor role is the authorization context Lambda will execute in; this is not the role Doppler will assume into to invoke the Lambda. We describe the minimum grants below, but there's a chance your role will require additional grants based on what service it is rotating and how you've architected your infrastructure.
- In your AWS account, navigate to IAM Roles
- Create Role
- Use AWS service for Trusted entity type
- Use Lambda for Use Case
- Under permissions, select AmazonS3ReadOnlyAccess and AWSLambdaVPCAccessExecutionRole
- Name your role and optionally provide a description
- Create
Lambda Function
Each service that is rotated uses a Lambda function powered by an open source rotator. You can use the same Lambda function to rotate n instances of the same service - i.e. you can use a single MySQL Lambda rotator to rotate as many MySQL secrets on as many MySQL instances as you'd like.
- In your AWS account - most likely in the region of the app or service you're rotating - navigate to Lambda
- Create a new function
- Name your function, ensuring the name begins with
Doppler_. This allows Doppler to use more finely scope access. - Set Node.js 20.x as the runtime
- Expand the permissions section to expose the
executor roleconfiguration. Choose the role you created in the section above . - Expand Advanced settings. Ensure Enable Code signing is checked and configure the settings as follows
- Code signing configuration: Create new configuration
- Description: Doppler code signing profile
- Signing profile ARN:
arn:aws:signer:us-east-1:299900769157:/signing-profiles/DopplerSecretAgents/7zfqycFf2B - Signature validation policy for code: Enforce
- Code location: Select the appropriate S3 URL from the table
- Enable VPC: You will most likely want your function to live in the same VPC as the resource being rotated. If not, you must ensure it can peer into the applicable VPC to reach the service being rotated.
- Create your function
- Scroll to the Runtime settings section and click edit. Update the handler with the corresponding value from the table below
| Service | Handler |
|---|---|
| MySQL (RDS or self-hosted) | apps/aws-mysql-rotator/dist/app.handler |
| Postgres (RDS or self-hosted) | apps/aws-postgres-rotator/dist/app.handler |
| MS SQL Server (RDS or self-hosted | apps/aws-mssql-rotator/dist/app.handler |
Increasing Lambda TimeoutThe default timeout for a Lambda function is 3 seconds. For larger instance sizes, that will probably work fine, but if your database is particularly busy or running on a smaller instance size, you may need to increase the Lambda function timeout.
You'll see an error like this during the setup process in the Doppler dashboard if you're running into this:
The Lambda agent timed out during execution. This can be caused by a network connection issue. Check your network configuration and verify that your Lambda can reach the database host.
IAM Role for Doppler to assume into
Policy
- In your AWS account, navigate to IAM Policies
- Click Create Policy
- Click the JSON tab
- Enter the following policy below after adding your Lambda's ARN and Code Signing Configuration ARN in the resource fields.
- Note:
lambda:UpdateFunctionCodeandlambda:GetCodeSigningConfigare optional but necessary if you'd like Doppler to be able to perform automatic updates. Otherwise, you'll need to manually upgrade to new versions. - The Code Signing Configuration was generated in Step 6 of Lambda Setup but the ARN was not displayed. You can retrieve this ARN via the AWS Console or using the CLI with
aws lambda list-code-signing-configs
- Note:
- Optionally add any tags
- Name your policy and click create policy
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"lambda:GetFunction",
"lambda:InvokeFunction",
"lambda:UpdateFunctionCode"
],
"Effect": "Allow",
"Resource": "YOUR_LAMBDA_ARN"
},
{
"Action": ["lambda:GetCodeSigningConfig"],
"Effect": "Allow",
"Resource": "YOUR_CODE_SIGNING_CONFIGURATION_ARN"
},
{
"Action": ["s3:GetObject"],
"Effect": "Allow",
"Resource": "arn:aws:s3:::doppler-keys-*/*"
},
{
"Action": ["s3:GetObject"],
"Effect": "Allow",
"Resource": "arn:aws:s3:::doppler-secret-agents-*/*"
}
]
}
Role
-
In your AWS account, navigate to IAM Roles
-
Click Create Role
-
Select AWS account for Trusted entity type
-
Check Another AWS account
-
For Account ID enter 299900769157
By default, AWS creates this trust relationship at the root level (i.e., using an ARN like
arn:aws:iam::299900769157:root), which grants permission to any user in Doppler's AWS account. Practically speaking, this is fine because this account is used specifically for production AWS integrations and is locked down securely. However, if you want to lock it down further, you can modify the ARN in the JSON definition toarn:aws:iam::299900769157:user/secret-agent-operatorso it's restricted to the specific user being used for rotated and dynamic secret operations. -
Check Require external ID
- Enter your workplace slug for the External ID value. You can obtain your workplace slug by visiting the Doppler dashboard. In the URL, grab the value after
/workplace/
- Enter your workplace slug for the External ID value. You can obtain your workplace slug by visiting the Doppler dashboard. In the URL, grab the value after
-
Attach the policy you created above.
S3 Gateway Endpoint
If your VPC does not have outbound access enabled, an S3 Gateway Endpoint is required to reach Doppler's public key on S3. If your VPC does have outbound access enabled, you can skip this step.
An AWS Gateway Endpoint enables your Lambda to communicate with our S3 bucket in order to retrieve our public key for payload signing verification.
- In your AWS account, navigate to VPC
- Click Endpoints and Create Endpoint
- Name your endpoint
- Leave Service Category as AWS Services
- In the Services section search for S3
- Select the endpoint with a type of Gateway. It will include the region in its name, e.g.
com.amazonaws.us-east-1.s3 - Select the VPC that the Lambda rotator resides in
- Select the appropriate route table from your VPC
- A policy is not required
Service Configuration
After the Lambda function is setup, you can move on to the next screen, where you'll configure service-specific settings. Select the appropriate page below to carry on
Automatic Lambda function updates
If the role provided to Doppler is given lambda:UpdateFunctionCode, we will automatically apply updates when available. If the lambda:UpdateFunctionCode is omitted, updates will need to be performed manually.
Manual Lambda function updates
If you do not grant lambda:UpdateFunctionCode and lambda:GetCodeSigningConfig to the Doppler IAM role, you will be responsible for manually updating your Lambda function.
- In the AWS console, navigate to the Lambda function
- In the Code Source section, click the Upload from drop-down and select Amazon S3 Location
- Enter the appropriate S3 URL for your AWS region from the here
Updated 3 months ago
