AWS Secrets Manager
Sync environment variables to AWS Secrets Manager.
This guide will show you how to set up automatic syncing of Doppler secrets to AWS Secrets Manager.
Prerequisites
- AWS Console Access
- AWS IAM access
- Ability to create IAM roles and Policies
- Ability to access IAM users
Authorization
Navigate to the project you would like to integrate, click Integrations from the Projects menu, then select AWS Secrets Manager to begin the authorization process.

If this is your first time setting up an integration with AWS Secrets Manager, you'll see the following screen
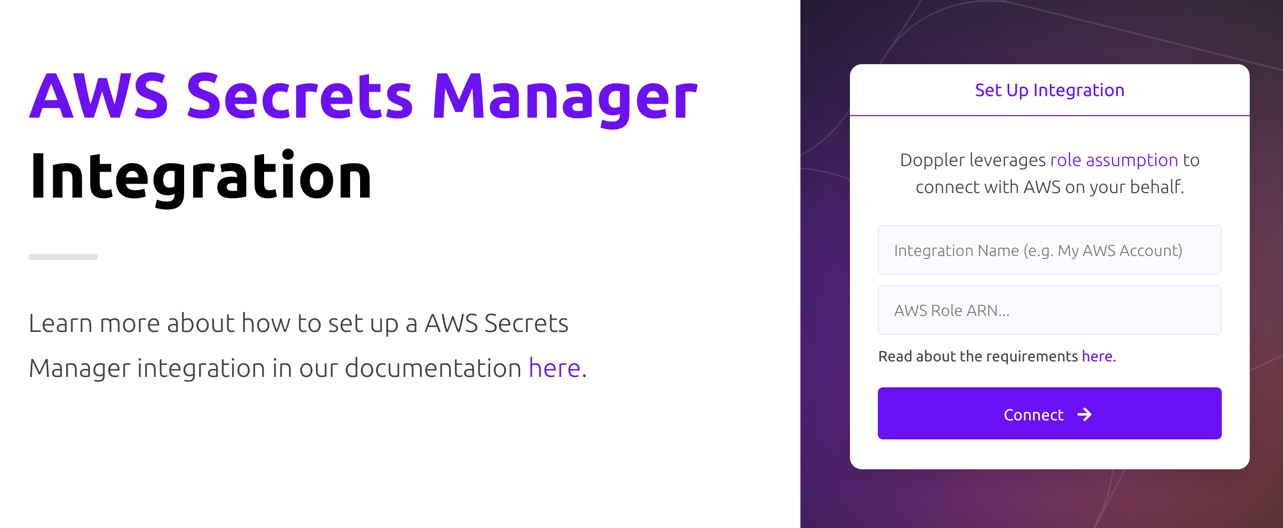
- Integration Name: A descriptor for the integration that will be displayed throughout Doppler
- AWS Role ARN: ARN for the role that Doppler will use to assume into your AWS account. Instructions are covered below
Role Assumption
Doppler uses an IAM role you provide to assume into your account. The role will leverage the policy below.
Policy
- Navigate to the Create New Policy section in the AWS IAM console
- Switch to the JSON tab
- Enter the appropriate policy from the options below. If you're using a custom KMS Key with your integration, then be sure to use the Custom KMS Key policy below.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowSecretsManagerAccess",
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret",
"secretsmanager:PutSecretValue",
"secretsmanager:CreateSecret",
"secretsmanager:DeleteSecret",
"secretsmanager:TagResource",
"secretsmanager:UpdateSecret"
],
"Resource": "*"
}
]
}{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowSecretsManagerAccess",
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret",
"secretsmanager:PutSecretValue",
"secretsmanager:CreateSecret",
"secretsmanager:DeleteSecret",
"secretsmanager:TagResource",
"secretsmanager:UpdateSecret",
"kms:DescribeKey",
"kms:ListAliases",
"kms:ListKeys",
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*"
],
"Resource": "*"
}
]
}{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowSecretsManagerAccess",
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret",
"secretsmanager:PutSecretValue",
"secretsmanager:CreateSecret",
"secretsmanager:DeleteSecret",
"secretsmanager:TagResource",
"secretsmanager:UntagResource",
"secretsmanager:UpdateSecret"
],
"Resource": "*"
}
]
}- Optionally provide tags
- Name your policy and hit create
Role
- Navigate to the create role section of the AWS IAM console
- Select AWS account for the Trusted entity type
- Select Another AWS account under An AWS account
-
Enter 299900769157 for the Account ID. This is Doppler's account ID.
By default, AWS creates this trust relationship at the root level (i.e., using an ARN like
arn:aws:iam::299900769157:root), which grants permission to any user in Doppler's AWS account. Practically speaking, this is fine because this account is used specifically for production AWS integrations and is locked down securely. However, if you want to lock it down further, you can modify the ARN in the JSON definition toarn:aws:iam::299900769157:user/doppler-integration-operatorso it's restricted to the specific user being used for integration operations.
-
- Under Options check Require external ID
- Enter your workplace slug for the External ID. You can obtain your workplace slug by visiting the Doppler dashboard. In the URL, grab the value after
/workplace/ - Leave require MFA unchecked
- Enter your workplace slug for the External ID. You can obtain your workplace slug by visiting the Doppler dashboard. In the URL, grab the value after
- Attach the policy you created above.
- Complete the role setup. When the role is created, click the link to it to view its details
- Copy its ARN
Configuration
Now choose the Config to sync, the AWS Region, Sync Strategy, Path (this is used to specify the secret or location we sync your secrets to), any Tags (optional) you may want to set on the secret(s), a KMS Key ID (optional: this uses the supplied KMS key when creating the secret in ASM), and finally choose whether metadata or tags are updated on sync.
The Sync Strategy option allows you to choose between Single-Secret and Multi-Secret. If Single-Secret is selected, then all secrets in the config will be synced to a single secret at the exact location you specify in the Path option (e.g., if Path is set to /yodaspeak/production then you'll end up with a single secret named /yodaspeak/production that contains all secrets in the config). If Multi-Secret is selected, then a separate secret will be created at the path location you specify for every secret in the config (e.g., if Path is set to /yodaspeak/production and you have a HOSTNAME secret, you'll end up with a secret at /yodaspeak/production/HOSTNAME that contains just the value of that secret).
If the metadata update option is enabled, Doppler will update the AWS secret metadata [e.g., KMS key] during every sync. If disabled, Doppler will only set secret metadata for new AWS secrets (note that this doesn't result in Doppler updating tags for existing AWS secrets). This can come into play in scenarios where you delete the sync, leave the secret in ASM, and then recreate the sync using the same location in ASM – since the secret already exists the KMS key won't be updated unless this option is enabled.
If the update tags on sync option is enabled, this will allow you to update the tags for your secrets by deleting the sync, choosing the option to leave your secrets in ASM, and then recreating the sync with a new set of tags. The "Upsert" option will leave any pre-existing tags in place and only add the new ones you specify. The "Replace" option will remove any pre-existing tags and replace them with the ones you specify in Doppler.
When using the Single-Secret sync strategy, Doppler uses the exact path you provide to determine where it should sync secrets to in ASM. For example, if Path is
/yodaspeak/production, the secret will be named/yodaspeak/production. This differs from how this worked previously where we would append/dopplerto the path that was supplied. Now, the path is used as supplied by the user.
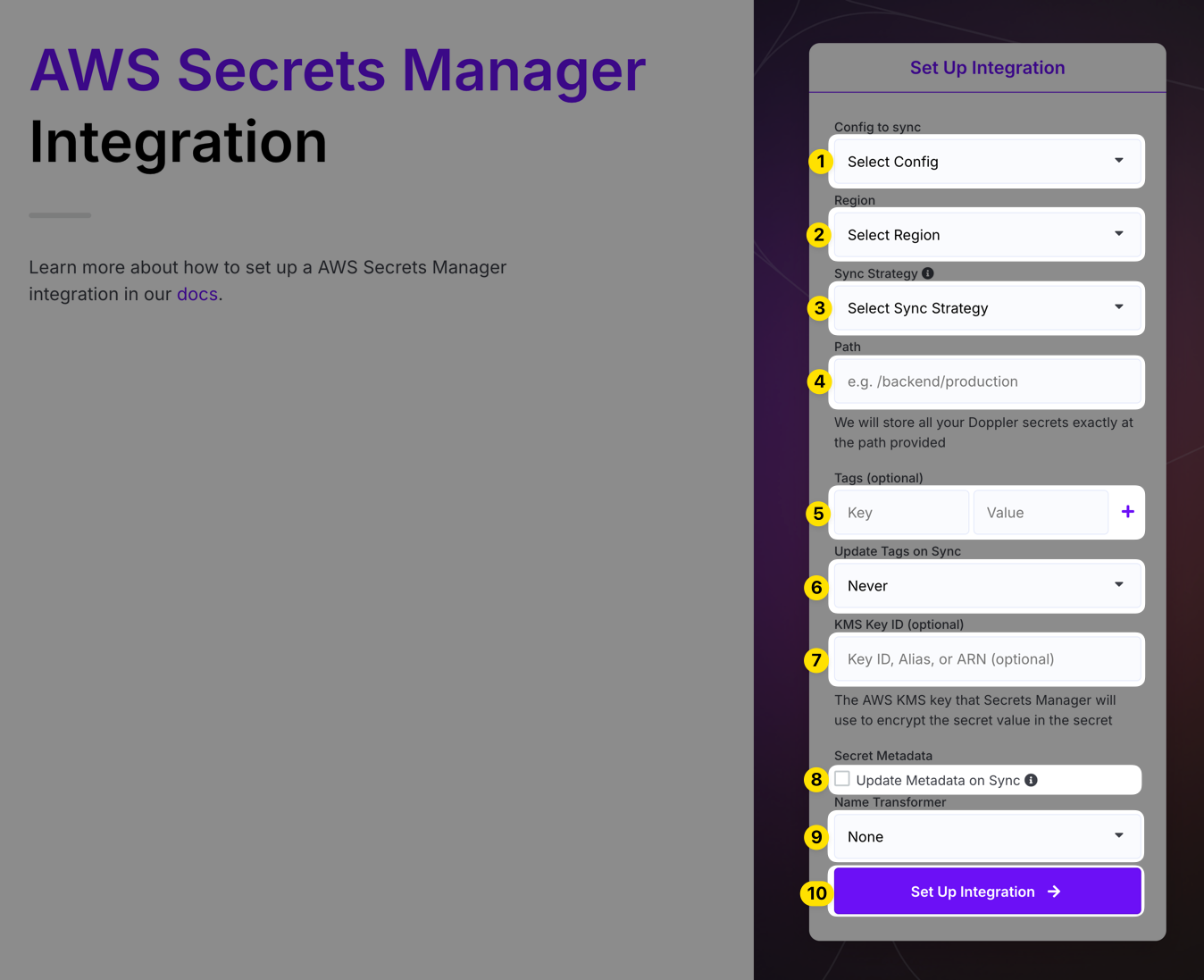
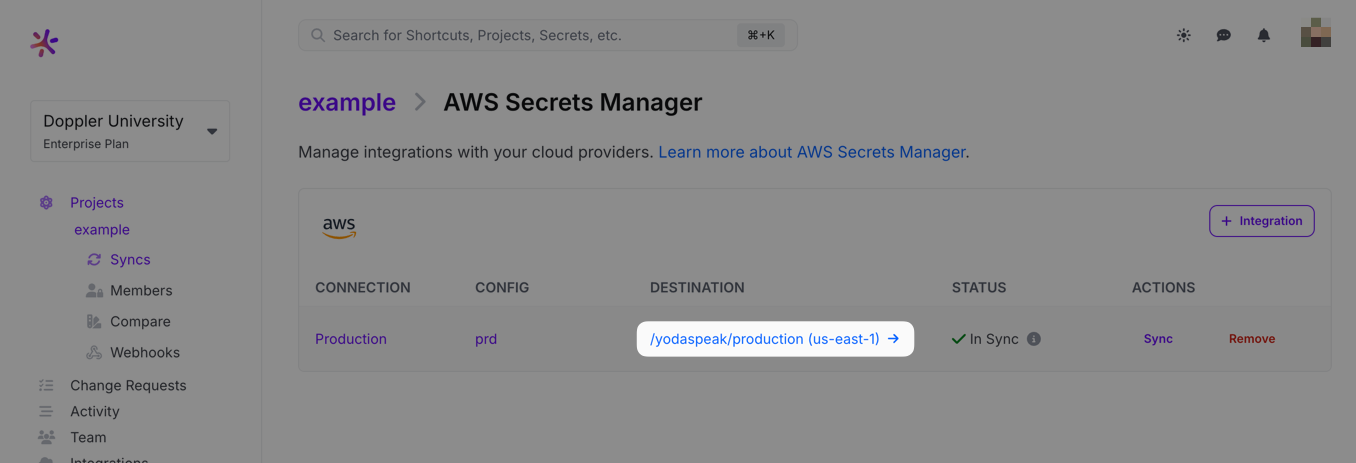
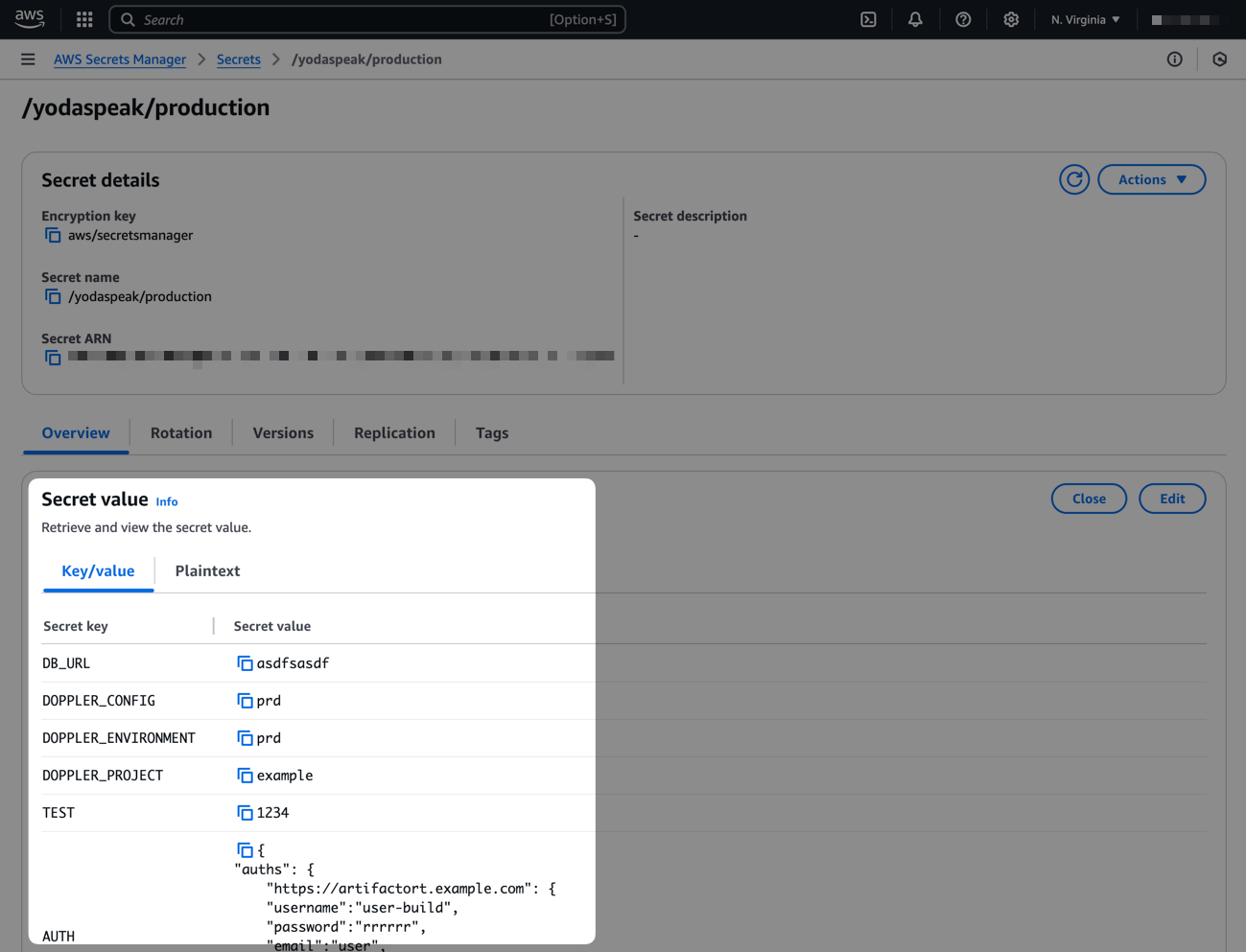
Click Setup Integration and Doppler will instantly sync your secrets to AWS! To confirm the integration is working correctly, you can view the secret created in Secrets Manager by clicking the DESTINATION link.
Importing Secrets
The AWS Secrets Manager integration doesn't currently support importing secrets. However, it's possible to import secrets programmatically using a script like this:
#!/bin/bash
# Check if jq is installed
if ! command -v jq &> /dev/null; then
echo "jq could not be found, please install jq to process JSON data."
exit 1
fi
# Check if aws is installed
if ! command -v aws &> /dev/null; then
echo "aws could not be found, please install the aws CLI."
exit 1
fi
# Check if doppler is installed
if ! command -v doppler &> /dev/null; then
echo "doppler could not be found, please install the doppler CLI."
exit 1
fi
# Configuration Variables
STRIP_SECRET_PATH="false" # strip path from secret name (e.g., changes 'some/path/secret-name' to 'secret-name')
DOPPLER_PROJECT_NAME="your-doppler-project-name"
DOPPLER_CONFIG_NAME="your-doppler-config-name"
AWS_SECRET_ARN="your-aws-secret-arn"
# Get the name of the secret from its metadata
secret_name=$(aws secretsmanager describe-secret --secret-id "$AWS_SECRET_ARN" --query 'Name' --output text)
# Strip the path from the secret name
if [ "$STRIP_SECRET_PATH" = "true" ]; then
secret_name=$(echo "$secret_name" | awk -F/ '{print $NF}')
fi
# Convert secret name to uppercase and replace disallowed characters with underscores
NORMALIZED_SECRET_NAME=$(echo "$secret_name" | tr '[:lower:]' '[:upper:]' | sed 's/[^A-Z0-9]/_/g')
# Fetch the secret value from AWS Secrets Manager
secret_value=$(aws secretsmanager get-secret-value --secret-id "$AWS_SECRET_ARN" --query 'SecretString' --output text)
SECRETS_JSON=""
# Determine if the secret value is valid JSON
if echo "$secret_value" | jq -e . &> /dev/null; then
# It's JSON, process all keys to uppercase and save
SECRETS_JSON=$(echo "$secret_value" | jq 'with_entries(.key |= ascii_upcase)')
else
# It's plaintext, use the formatted secret name
SECRETS_JSON="{ \"$NORMALIZED_SECRET_NAME\": \"$secret_value\" }"
fi
# Check if the transformation was successful
if ! ( echo "$SECRETS_JSON" | jq -e . &> /dev/null ); then
echo "Failed to process JSON data."
exit 1
fi
# Upload the JSON file to Doppler
doppler secrets upload --project $DOPPLER_PROJECT_NAME --config $DOPPLER_CONFIG_NAME <(echo "$SECRETS_JSON")If the secret you're importing contains many key/value secret pairs, it will import all of those as separate secrets. If the secret is a plaintext secret, it will import that as a single secret where the name is the normalized path (i.e., it's converted to uppercase and has any character that isn't alphanumeric converted to an underscore). For example, devops/some-app-name/dev/stripe-api-key would be imported as DEVOPS_SOME_APP_NAME_DEV_STRIPE_API_KEY. You can set STRIP_SECRET_PATH to true to have that imported as STRIPE_API_KEY instead.
Amazing Work!You've successfully set up the Doppler AWS Secrets Manager integration! Every time you update your secrets in Doppler, we will automatically update them in AWS Secrets Manager.
Updated 4 months ago
